Digital trust has become the invisible currency of modern business. Every authentication, every transaction, and every user session relies on one simple assumption: encryption works. But what happens when that foundation begins to crack under the weight of quantum computing?
Welcome to the era where quantum technology doesn’t just innovate; it disrupts trust itself.
🔹 The Looming Quantum Threat to IAM
Quantum computing is no longer a far-off concept; it’s at the threshold of commercialisation. Giants like IBM, Google, and China’s Baidu have already demonstrated that machines can surpass classical limits.
While this opens the door to unprecedented data processing power, it also poses a catastrophic risk to current cryptographic standards, the same ones that IAM systems depend on.
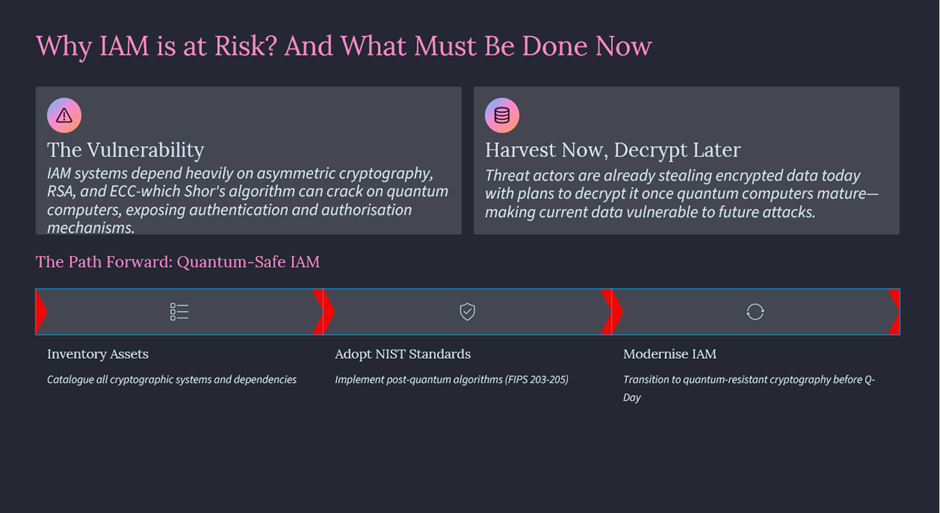
Why this matters for IAM:
Most Identity and Access Management (IAM) frameworks operating today rely on the backbone of public-key cryptography; most notably, RSA and Elliptic Curve Cryptography (ECC). These algorithms have safeguarded digital identities for decades, ensuring that everything from authentication tokens to SSL certificates remains trusted and tamper-proof. However, this security model was designed in a world where computational limits kept brute-force attacks impractical.
That world is changing. With the advent of quantum computing, the cryptographic walls that protect IAM systems are facing an existential threat. Algorithms like Shor’s Algorithm, a quantum algorithm developed by mathematician Peter Shor, can, in theory, factor large prime numbers exponentially faster than classical computers. In simpler terms, what would take a traditional computer hundreds or even thousands of years to decrypt could be solved by a sufficiently powerful quantum computer in minutes.
This has profound implications. Once quantum computers reach full-scale capability, they could break the encryption standards that underpin modern identity systems. Digital certificates, secure sessions, OAuth tokens, and even federated identity protocols such as SAML or OpenID Connect could all be rendered vulnerable. Imagine a scenario where every encrypted user credential, every secure API handshake, and every digital identity stored in your IAM ecosystem becomes readable text; accessible to anyone with quantum processing power. In essence, the coming quantum era isn’t just a shift in computing; it’s a redefinition of digital trust. IAM leaders must now prepare for a world where today’s encryption could become tomorrow’s exposure.
🔹 Real-World Signals: Who’s Taking Quantum Seriously
Global Leaders Taking Charge

1. United States: NIST’s Quantum-Safe Blueprint
The U.S. National Institute of Standards and Technology (NIST) has finalised a new set of Post-Quantum Cryptography (PQC) algorithms designed to withstand quantum-level attacks. Among these are CRYSTALS-Kyber for encryption and CRYSTALS-Dilithium, Falcon, and SPHINCS+ for digital signatures.
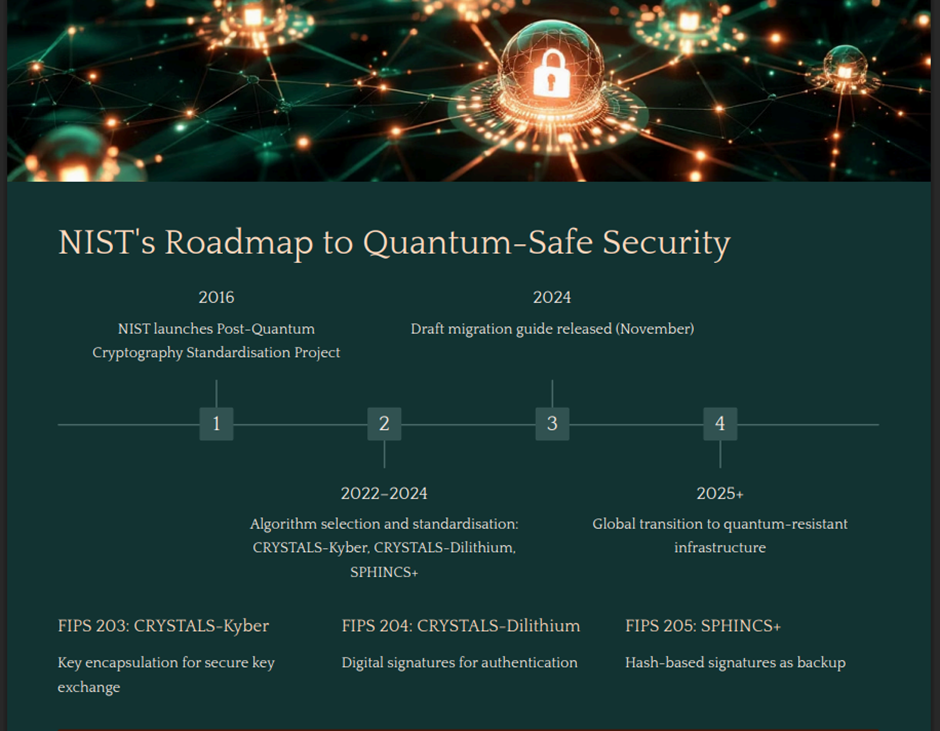
These algorithms are being positioned as the future standard for federal agencies, financial institutions, and private enterprises.
NIST’s framework will serve as a global reference model for securing data, identity credentials, and communications in a post-quantum world.
The move signals that the U.S. is preparing IAM systems that will remain resilient for decades.
2. Europe: Quantum Communication at Scale

The European Union is investing heavily in quantum-safe communication infrastructure through its EuroQCI (European Quantum Communication Infrastructure) initiative.
The project aims to connect all 27 EU member states using quantum encryption technologies.
By integrating Quantum Key Distribution (QKD), it ensures tamper-proof authentication between government and corporate networks.
This quantum-secured backbone will ultimately support identity management and cross-border trust services, paving the way for interoperable digital identity frameworks under eIDAS 2.0.
3. Asia-Pacific: Building Quantum-Ready Economies

India’s Quantum Mission (2023–2031) has been announced to strengthen quantum computing, cryptography, and communication capabilities. Government institutions like C-DAC and DRDO are collaborating to test quantum-safe encryption layers for defence and public networks.
China has taken a parallel lead by deploying quantum satellites (like Micius) to test global-scale quantum key distribution, aiming for an ultra-secure communication framework.
Japan and South Korea are partnering with universities and tech giants like NTT and Samsung to integrate quantum-safe encryption models within IoT and smart manufacturing systems.
Industry Front-Runners Future-Proofing IAM
1. Google’s Quantum-Resistant Chrome
Google has started experimenting with quantum-resistant keys in Chrome, introducing hybrid key encapsulation mechanisms (KEMs) to secure HTTPS traffic.
This ensures that even if quantum computers arrive tomorrow, web sessions and identities won’t be decrypted retroactively.
It’s a monumental step toward post-quantum web authentication and will eventually set a standard for browser-based IAM.
2. Financial Powerhouses Going Quantum-Safe
Global banks and payment networks are treating quantum readiness as a board-level priority.
JP Morgan Chase, in collaboration with Toshiba and IBM, is testing quantum-safe networks for secure transaction pipelines and identity validation.
Mastercard and Visa are evaluating post-quantum cryptographic protocols for digital identity authentication in cross-border payments.
These pilots aren’t experiments; they’re blueprints for next-generation IAM that will guard against credential theft and identity fraud in high-value ecosystems.
3. Cloud and Identity Platforms Adapting for PQC
Leading IAM and cybersecurity vendors like Okta, Microsoft Entra, and CyberArk are already exploring quantum-resilient authentication mechanisms.
They’re working to embed quantum-safe encryption into federated identity systems and privileged access management.
These companies are re-engineering zero-trust frameworks to withstand quantum-level breaches, ensuring session integrity and key lifecycle protection.
Why This Matters for IAM Leaders
The global movement toward quantum-safe standards isn’t just about cryptography; it’s about future-proofing trust frameworks. Every organisation that relies on identity, from governments to startups, will need to revisit how they issue, store, and verify credentials.
Key takeaways for IAM professionals and CISOs:
- Start early: Transitioning to PQC algorithms takes time and planning.
- Adopt hybrid encryption: Use classical + quantum-safe methods during the migration period.
- Educate stakeholders: Quantum readiness must be understood from the C-suite down to engineering.
- Collaborate globally: Engage in standardisation initiatives like NIST, ISO, and ETSI for unified IAM practices.
The organisations leading the charge aren’t just defending data; they’re defending the concept of digital identity itself. By embracing quantum-safe architectures, they’re securing the foundation of online trust, enabling a future where IAM systems remain both resilient and relevant; no matter how powerful quantum computing becomes.
🔹 The Enterprise Reality Check: Pain Points Ahead
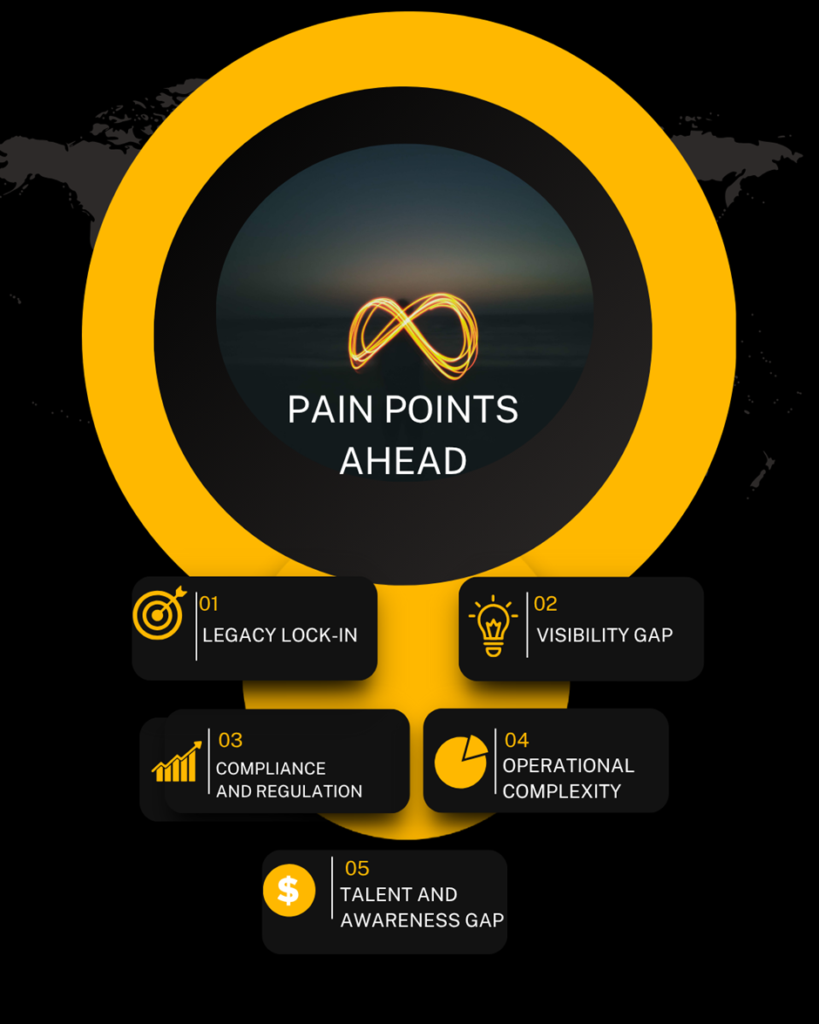
Despite growing awareness, most IAM teams remain underprepared. Here are the most critical pain areas enterprises are facing:
1. Legacy Lock-In
Existing IAM architectures are deeply integrated with outdated cryptography standards.
Migrating to PQC-ready models involves costly system overhauls and vendor dependencies.
2. Visibility Gap
Many organisations don’t know which parts of their identity infrastructure are vulnerable.
Cryptographic inventory audits are rare, leaving unknown exposure points.
3. Compliance and Regulation
Data protection frameworks like GDPR and India’s DPDP Act are silent on PQC-readiness.
This regulatory lag could create confusion and non-compliance risks during transition.
4. Operational Complexity
Integrating PQC into federated identity environments (like SSO, OAuth, SAML) is non-trivial.
Enterprises fear disruption to daily authentication flows.
5. Talent and Awareness Gap
Cybersecurity teams often lack quantum literacy.
This slows down internal alignment and strategic adoption.
🔹 Building a Quantum-Ready IAM Strategy
Quantum disruption doesn’t have to mean chaos; it can be the push enterprises need to modernise and reimagine trust frameworks.
Here’s how to start:
✅ 1. Conduct a Crypto Inventory
Identify all applications, APIs, and IAM components using classical cryptography.
Tag high-value identity assets (admin credentials, authentication servers).
✅ 2. Transition to Crypto-Agile Architecture
Adopt a modular IAM design where cryptographic algorithms can be swapped easily.
Use vendors supporting PQC agility (like Saviynt, Okta, ForgeRock with adaptive encryption).
✅ 3. Pilot Post-Quantum Algorithms
Experiment with Kyber (for key encapsulation) and Dilithium (for digital signatures).
Monitor performance, integration complexity, and ecosystem compatibility.
✅ 4. Collaborate with Ecosystem Partners
Join quantum readiness consortiums (like ETSI or Quantum-Safe Security Working Group).
Collaborate with academia and startups advancing PQC innovations.
✅ 5. Educate and Upskill Teams
Train IAM engineers on quantum-safe migration paths and crypto lifecycle management.
Include PQC awareness in organisational cybersecurity drills.
🔹 The Human Element: Rebuilding Digital Trust
At its core, Identity and Access Management (IAM) has never been just about systems, protocols, or cryptographic keys; it’s about human trust in digital ecosystems. Every login, authentication, or digital handshake represents a silent agreement: your identity is genuine, your data is safe, and the system will protect you. But in the quantum age, that trust model is being stress-tested like never before.
Recent reports by Gartner (2024) and IBM’s Quantum Safe Roadmap indicate that nearly 60% of global enterprises have not yet started assessing the quantum vulnerability of their IAM systems. This gap is alarming because a single compromised identity could open the floodgates to massive data breaches; especially when encrypted records, stolen today, could be decrypted tomorrow with quantum power.
To rebuild trust, organisations need IAM systems that are transparent but tamper-proof, ensuring visibility without compromising privacy. Authentication must evolve to become seamless yet quantum-resilient, leveraging post-quantum cryptographic algorithms that protect both user convenience and data integrity. And most importantly, humans must remain at the centre; designing IAM not just for compliance, but for confidence. Because when trust becomes the most valuable digital currency, the true measure of security lies not in encryption alone, but in how confidently people rely on it.
Decoded: The Quantum Shift Is an Opportunity, not a Crisis
Yes, the quantum era will challenge everything we know about identity, trust, and digital security, but it will also ignite the next great evolution in Identity and Access Management (IAM). Instead of seeing it as a looming danger, forward-thinking organisations are beginning to recognise it as an opportunity; a call to rebuild digital trust from the ground up.
As quantum computing matures, the organisations that stay ahead will not be those merely reacting to threats, but those architecting proactive defence strategies. The future of IAM will not only focus on safeguarding credentials but also on designing identity ecosystems resilient enough to adapt to unpredictable cryptographic realities.
Here’s how the transformation is likely to unfold:
- Post-Quantum Cryptography Integration: Businesses will begin migrating toward quantum-resistant algorithms like CRYSTALS-Kyber and Dilithium, ensuring long-term confidentiality and authentication integrity.
- Decentralised Identity Models: Self-Sovereign Identity (SSI) frameworks will rise as organisations push for greater user control and privacy-preserving authentication.
- Zero-Trust Reinforcement: The Zero Trust architecture will evolve further, driven by continuous verification, contextual risk assessment, and machine learning-based anomaly detection.
- AI-Augmented Identity Governance: Artificial intelligence will power adaptive access models capable of dynamically identifying and responding to emerging quantum-level threats.
- Global Collaboration on Standards: Cross-border cooperation will become crucial to establish quantum-safe identity protocols, much like how the internet once standardised SSL/TLS.
In the end, quantum computing doesn’t just disrupt; it redefines. It’s forcing CISOs, IAM leaders, and digital architects to ask deeper questions: How do we define trust in a world where even encryption can be outsmarted? How do we ensure identity remains authentic when computation itself changes its meaning?
The question is no longer if quantum disruption will arrive; it’s how ready your IAM ecosystem will be when it does.






