A. What is Quantum computing vs. Quantum Cryptography?
Quantum computing is not a novel theory anymore infact it’s unfolding faster than we estimated. As research labs and tech giants, gigs, and pharmaceutical farms edge closer to real-world encrypted cryptography; in reality, the encryption over which we rely today faces an existential risk.
Public-key encrypted algorithms like RSA and ECC are the backbone of digital identity, in reality, both cryptographies are now holding space as an outdated cult. This isn’t just an IT concern rather it’s a direct hit on Identity and Access Management foundations but already dragging their feet on global encrypted algorithms.
A non-negotiable revolution in cybersecurity is rising at a breakneck speed so tech leaders should strategize their approach with the apposite use of Post-Quantum Cryptography. For IAM leaders, there is no right time but there’s always a bad threat event that could be waiting at your doorstep. Being idle and watching from the sidelines could put the situation into an unbearable cost game; likewise, take the plunge into reinforcing identity systems with post-quantum-cryptographic (PQC) protocols which will make future IAM systems fully quantum computer immune. A non-negotiable revolution in cybersecurity is speeding up every second, likewise the required action should be positively taken without relying on outdated IAM norms.
B. Decoding Quantum Computer usage in real-world IAM- why stopping its progress is a serious topic in the tech world today
How Quantum Computers pose threat attacks to present IAMs
Quantum computers are posing attacks at an unchecked speed and raising daily emerging cybersecurity threats. Quantum computing simply relies on the principle which exploits the immense processing power of quantum machines by breaking traditional encrypted algorithms like RSA and ECC. These attacks can render today’s digital identity systems vulnerable in the blink of an eye, exposing authentication mechanisms, data, and credentials to unauthorized access.
‘Quantum computers aren’t just faster but they’re a whole new breed of problem-solvers’, well this was the initial essence that paved its way to reach the vulnerable areas of IAM systems. What feels secure today is about to flip it on its head tomorrow. Using Shor’s algorithm, these machines could tear through RSA keys, dismantle ECC, and even crack Diffie-Hellman like it’s child’s play. We’re not talking theory anymore but adaptive user authentications like digital signatures, encrypted credentials, and SSO tokens could be harvested today and exposed later. And that’s the real twist in trusting Quantum Computing as a mere resource of problem-solving when it’s not only fully performing as decryption but indulging proactively into user identity forgery at scale. If your IAM isn’t future-proofed with quantum cryptography answers, then better an organisation should consider their IAM as already in a vulnerable stage.
C. Why Quantum-Safe IAM has become the cement for the future foundation of cybersecurity and needs to be adapted right now
To beat the uncontrollable triumph of the Quantum trend for a secured user trust environment, prior actions have to be efficiently made from the end of every IAM leader. Pillars that speed up this process of diffusing the exploding bomb of quantum rule are –
- Post-quantum cryptography isn’t a matter of a quick fix
Transitioning to quantum-resilient IAM takes time. From evolving standards to vendor readiness, cryptographic migration is a multi-year journey and hence we need to kick-start the process of Quantum cryptographic solutions in today’s IAM algorithms.
- IAM is Deeply Rooted in Legacy Encryption
RSA, ECC, and SHA-based algorithms form the backbone of today’s identity infrastructure and the delay in adaptive Quantum cryptography in IAM makes it highly vulnerable in a quantum-ready world.
- Compliance Isn’t Optional Anymore
With NIST and global regulators pushing for quantum-safe frameworks, delaying action risks non-compliance and security exposure.
- Your Data Is Already susceptible to threat
What’s safeguarded today in digital lockers like your tokens, certs, and credentials, has a higher chance of getting misused as they can be cracked tomorrow by quantum attacks. The threat isn’t hypothetical; ‘Saving it for a rainy quantum day’
D. Who introduced the soul of ‘Post-Quantum Cryptography’ in future cybersecurity landscape – Origin of the future of Identity and Access Management system
Post-Quantum Cryptography (PQC) isn’t just a tech upgrade but actually, it’s the new firewall for the quantum era. Built on lattice-based, hash-based, and multivariate polynomial hard problems, these next-gen encryption and signature algorithms are engineered to resist both classical and quantum hacks. NIST (National Institute of Standards and Technology) has gained importance for bringing the concept of Quantum Cryptography into focus by recognizing the threat culture posed by quantum computers to current encryption norms.
NIST finalized its first standard set in 2022, and names like CRYSTALS-Kyber (for key encapsulation) and CRYSTALS-Di lithium (for digital signatures) became the new backbone of quantum-resilient IAM.
E. How to save the future user authentication trust with Quantum immune IAMs
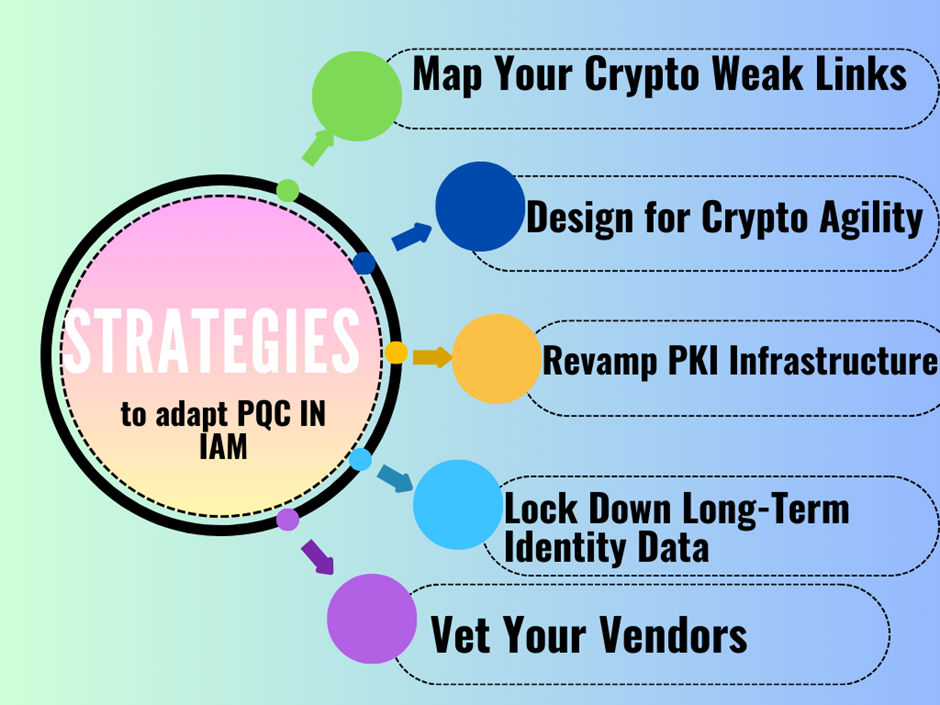
- Map Your Crypto Weak Links
Run a deep audit across IAM touchpoints like SSO, MFA, federated IDs, and device certs which will immediately to flag any RSA, ECC, or SHA-based systems at risk.
- Design for Crypto Agility
Future-proof your stack with hybrid models that support smooth transitions to PQC algorithms promising no messy overhauls later.
- Revamp PKI Infrastructure
Lay the groundwork for PQC-ready keys, digital signatures, and certificate lifecycle upgrades (X.509 included).
- Lock Down Long-Term Identity Data
If you own sensitive assets like archived logs and legal identities. Encrypt them now with quantum-safe tools before they’re sitting ducks.
- Vet Your Vendors
Choose IAM solutions such as CIAM, IGA, PAM, MFA as they work with a visible and strategic roadmap toward PQC integration.
F. Tracking the places where Quantum hits IAM the deadliest
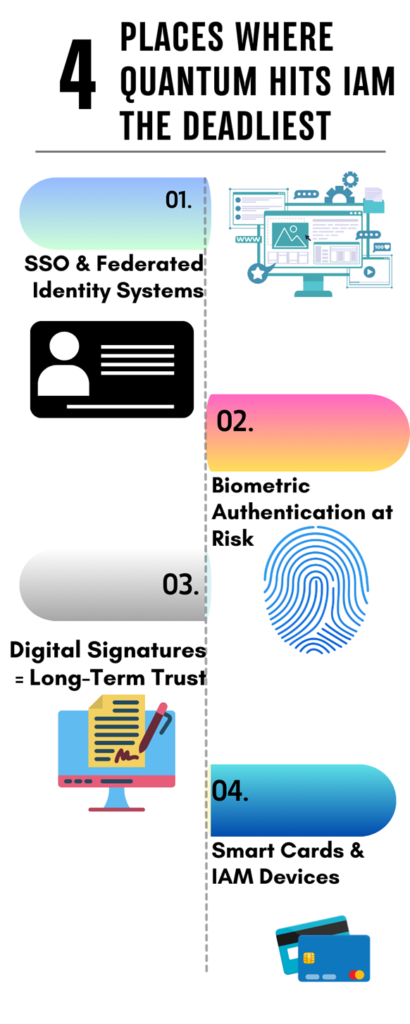
- SSO & Federated Identity Systems
RSA/ECC still powers most SAML, OAuth, and OpenID flows. Without PQC, your token exchange could be wide open tomorrow.
- Biometric Authentication at Risk
Those retina scans and fingerprint templates are actually an open secret why? Because they if not encrypted with quantum-safe methods, they’re simply future breach material.
- Digital Signatures = Long-Term Trust
Provisioning logs, approval workflows, and audit trails demand Post Quantum Cryptographic (PQC)-grade signatures to preserve authenticity over time. Hence wasting time will equal losing the confidential treasures of an organization
- Smart Cards & IAM Devices
From hardware tokens to secure elements that take PQC into the core of risk falling behind the quantum curve.
G. What’s holding the system back from adapting to fully PQC immune IAM
- Performance Trade-offs
Some post-quantum algorithms demand heavier computing and bulkier key sizes. It’s not only about the plug-and-play system but while adapting this algorithm IAM needs rigorous testing and fine-tuning.
- Legacy Lock-In
Traditional IAM systems weren’t built for crypto-agility so when you try to fix it for PQC it will collapse; isn’t just a normal upgrade but it’s a structural overhaul.
- Uncertainty in timelines
The quantum clock is ticking unevenly. But those who pivot early build resilience, win trust and outpace the reactive crowd.
H. Strategic Moves that IAM Leaders can achieve while ignoring the challenges in the PQC Shift
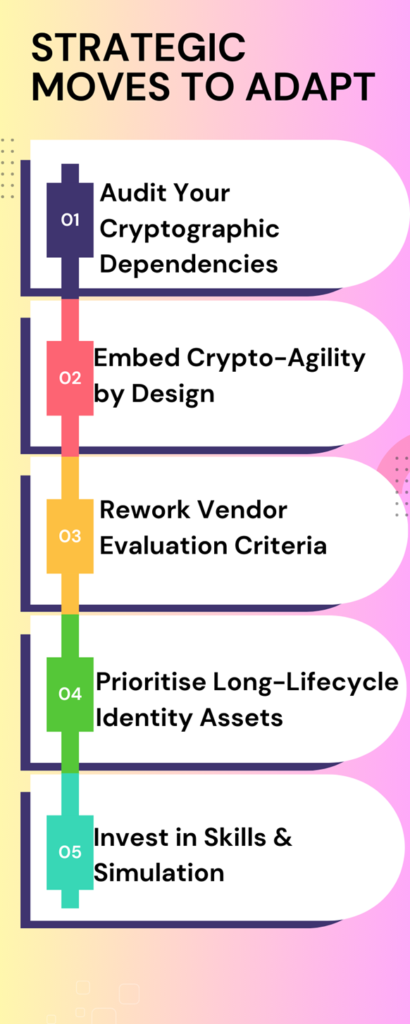
- Audit Your Cryptographic Dependencies
Begin with a deep scan of all IAM touchpoints such as SSO flows, digital signatures, device certificates, and federated protocols. Pinpoint where RSA, ECC, or SHA-based mechanisms are hard coded. A strong auditing could bring an unprecedented opportunity to make the present IAMs work with the norms of PQC.
- Embed Crypto-Agility by Design
Don’t wait for disruption instead try to build architectures that support flexible algorithm swaps.
For example, you can take Hybrid cryptography (classical + PQC) offers a phased, risk-managed approach.
- Rework Vendor Evaluation Criteria
Partner only with IAM, CIAM, and IGA vendors aligned with NIST’s PQC standards. Ask for roadmap transparency and don’t sit stress-free only upon assuming compatibility.
- Prioritize Long-Lifecycle Identity Assets
Re-encrypt sensitive archives, legal credentials, and biometric hashes now. These are the most vulnerable identity treasures ignoring which could be like “Collect now, crack later” quantum threats.
- Invest in Skills & Simulation
Understand the smart moves by upskilling your IAM and Public Key Infrastructure (PKI) teams in PQC principles. Run sandbox tests viz; Web Browser Sandboxing, Virtual Machine (VM) Sandboxing, Application Sandboxing, etc to monitor performance shifts before full production deployment.
Future-Proofing IAM: Embracing the Quantum Shift with Confidence
Post-quantum cryptography (PQC) isn’t just another checkbox in cybersecurity—it’s a strategic imperative for IAM systems that aim to stay resilient in a world where quantum threats are no longer theoretical. The transformation toward quantum-immune IAM is not about fear-mongering but about foresight. Leaders who begin now – auditing systems, embracing crypto-agility, and aligning with NIST-backed PQC standards – will be the ones safeguarding user trust, compliance, and digital sovereignty in the years ahead.
Yes, the road to PQC readiness involves complexity – from reengineering legacy infrastructure to managing performance trade-offs—but delaying this journey is far riskier. The cryptographic race is on, and quantum computing is gaining ground. IAM leaders must see this shift as an opportunity: to rebuild identity frameworks that are more agile, secure, and future-aligned.
This is your moment to lead from the front—by not just adapting to change but driving it. Secure your identities today so that they remain unbreakable tomorrow.








