INTRODUCTION
Enterprises today manage an explosion of identities: employees, partners, contractors, machines, service accounts, APIs, workloads, and bots. As digital ecosystems expand across multi-cloud, hybrid networks, and SaaS platforms, identity has become the real perimeter. Yet most organisations still operate with fragmented IAM systems that were never designed for today’s distributed environments.
This gap is exactly why global enterprises are transitioning toward an Identity Mesh Strategy. This modular, scalable, and intelligence-driven approach unifies identity services across the business without forcing a single monolithic IAM stack.
Why Enterprises Need an Identity Mesh Strategy
Identity Sprawl Has Outpaced Traditional IAM
Modern enterprises today manage ten times more machine identities than human identities, and this imbalance is growing at an unprecedented pace as digital transformation accelerates. Every API, microservice, container, workload, bot, script, serverless function, and automated pipeline introduces a new machine identity that must be authenticated, authorised, monitored, and governed. Unlike human identities, which follow predictable lifecycle events: hire, role change, exit, machine identities multiply rapidly and often operate without direct human oversight. This leads to unmanaged service accounts, orphaned credentials, hardcoded secrets, unrotated certificates, and non-compliant access paths that attackers can exploit with relative ease. In the absence of a unified identity architecture, these machine identities remain scattered across cloud providers, legacy systems, CI/CD tools, and application stacks, creating blind spots and governance gaps. As a result, enterprises face increased operational risk, inconsistent policy enforcement, and expanding attack surfaces. This is why modern IAM must adopt a distributed, mesh-driven approach capable of handling this explosive machine identity growth with precision, scalability, and real-time intelligence.
- Multi-cloud users
- Microservices and container workloads
- DevOps pipelines
- SaaS integration identities
- Third-party vendor identities
An Identity Mesh acts as an “identity fabric” that links these otherwise disconnected components without replacing existing investments.

Zero Trust Depends on Consistent Identity Signals

Zero Trust requires:
- Continuous risk assessment
- Context-based access decisions
- Unified monitoring
- Real-time identity posture
Without an identity mesh, critical identity signals remain trapped in isolated systems: legacy directories, cloud-native IAM tools, custom application databases, and disparate security platforms. Each system holds only a fragment of the user or machine’s true identity posture, which means access decisions are often made with incomplete or outdated information. This fragmentation slows down authentication processes, weakens authorisation accuracy, and creates blind spots that adversaries can exploit. For example, privileged access risks may go undetected if behavioural anomalies in one environment are not visible to another. In high-stakes scenarios such as just-in-time access or adaptive authentication, these gaps result in inconsistent enforcement and increased vulnerability. However, when an enterprise adopts an identity mesh, all identity signals, behavioural, contextual, and risk-based, flow into a unified layer. This creates a consistent identity state across clouds, applications, endpoints, and hybrid environments. With this unified intelligence, Zero Trust becomes truly operational at scale, enabling continuous verification, policy alignment, faster response to anomalies, and a dramatically stronger overall security posture.
Hybrid & Multi-Cloud Demands Interoperability
According to industry data, around 90% of enterprises operate in a multi-cloud environment.
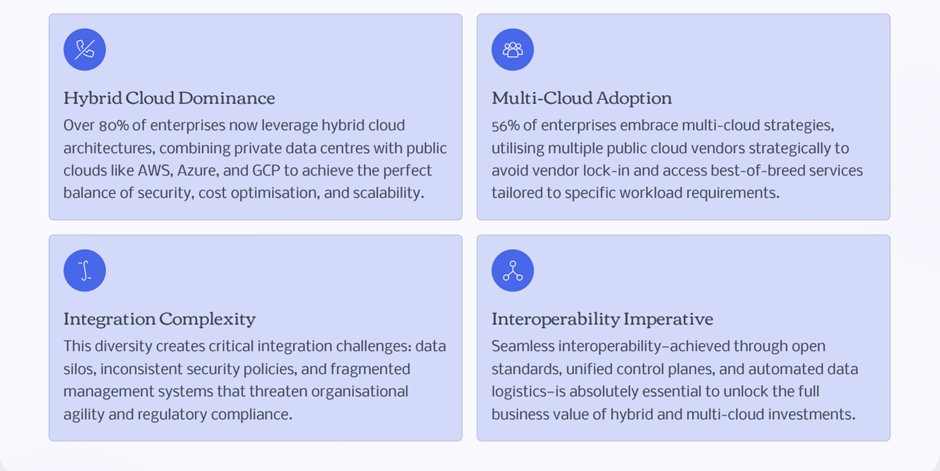
The challenges include:
- Multiple IAM vendors
- Different authentication policies
- Inconsistent provisioning logic
- Divergent governance workflows
- An Identity Mesh overlays these environments and provides:
- Standardised controls
- Shared policy execution
- Unified audit reporting
- Connected identity lifecycle events
This eliminates the “identity fragmentation tax.”
Identity Mesh Reduces IAM Costs & Technical Debt
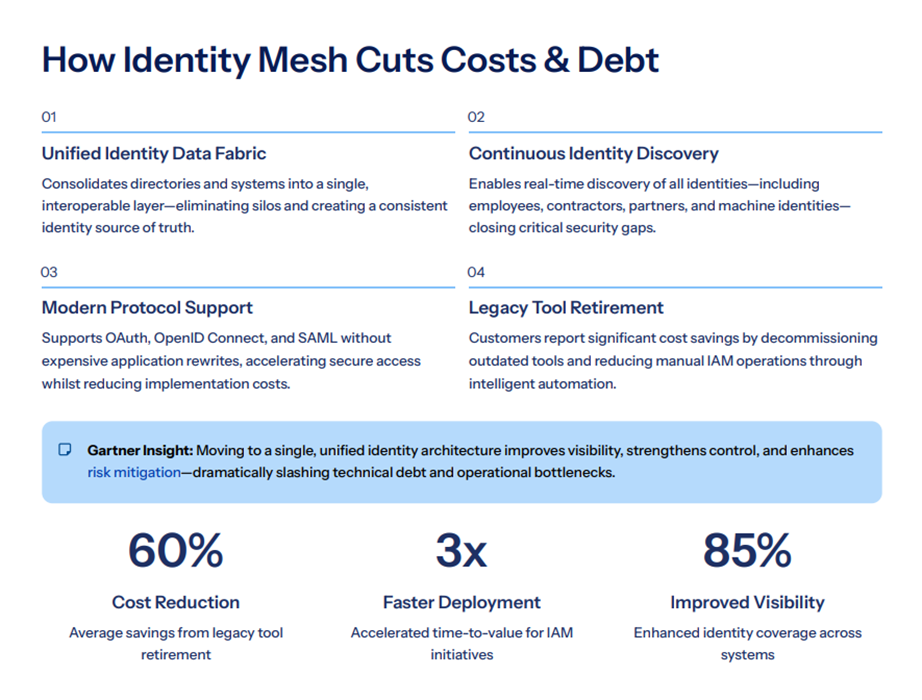
Enterprises spend heavily on:
- Custom connectors
- Manual provisioning
- Redundant toolsets
- Compliance-driven rework
With a mesh:
- Integration reusability increases
- Governance becomes automated
- IAM teams reduce operational overhead
- Audit and certification cycles shorten
Multiple enterprises adopting identity mesh report up to 40–60% reduction in operational IAM costs.
Machine Identity Management Requires a Distributed Model
Machine identities grow at nearly two times the rate of human identities.
A mesh supports:
- Short-lived credentials
- Automated certificate rotation
- API-to-API authentication
- Workload access policies

It provides a dynamic, distributed identity control plane suited for cloud-native architectures.
AI-Driven Attacks Require AI-Enhanced Identity Intelligence
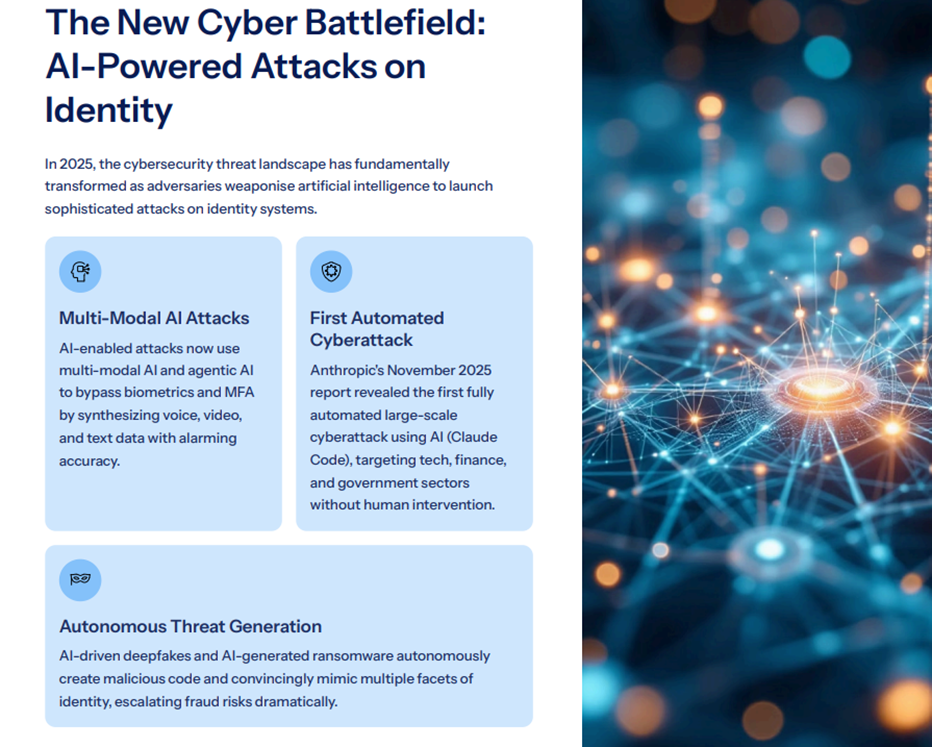
AI-generated threats, deepfake voice, synthetic identities, credential-stuffing bots, automated phishing frameworks, and AI-driven reconnaissance tools are evolving far faster than legacy IAM systems can handle. Traditional identity controls were designed around predictable human behaviour and static credential patterns. Today, adversaries use machine-learning algorithms to mimic user actions, bypass authentication prompts, and generate synthetic digital footprints that appear legitimate to outdated systems. Deepfake audio can successfully impersonate executives during high-value transactions, while generative models can produce convincing identity documents that can bypass onboarding workflows. Similarly, automated bots can test millions of stolen or guessed credentials in minutes, probing authentication systems for weaknesses at a scale no human team can monitor manually. These attacks exploit the gaps created by siloed identity data and slow, rule-based verification processes.
In contrast, an identity mesh architecture enables continuous, real-time identity intelligence by correlating behaviour, context, device posture, access history, and risk signals across multiple systems.
This creates a dynamic defence layer capable of detecting anomalies that static IAM tools miss. As attackers become increasingly sophisticated with AI, enterprises must adopt equally advanced and adaptive identity architectures to stay ahead of emerging threats.
Identity Mesh enables:
- Real-time anomaly detection
- Continuous behavioural analytics
- Adaptive risk scores
- Automated remediation
The system makes access decisions based on context, behaviour, and identity posture, not just static authentication.
Compliance & Governance Become Streamlined
Regulations such as GDPR, HIPAA, PCI-DSS, SOX, ISO 27001, and India’s DPDP Act place increasing pressure on enterprises to maintain unified, transparent, and auditable identity governance. Each of these frameworks demands demonstrable control over who has access to what, how that access was granted, when it was used, and whether it aligns with the principle of least privilege. However, most enterprises operate across a fragmented landscape of directories, cloud IAM tools, on-prem applications, SaaS platforms, and custom-built systems; each holding its own version of identity and access data. This fragmentation results in inconsistent reporting, duplicated access rights, orphaned accounts, and gaps in certification cycles. Auditors frequently encounter incomplete logs or mismatched access histories, forcing security teams to rely on manual reconciliation that is error-prone and time-consuming. An identity mesh addresses this by creating a unified governance layer that aggregates identity signals, centralises policy enforcement, and standardises audit trails across all environments. It provides real-time visibility into entitlements, toxic combinations, segregation-of-duty violations, and anomalous access patterns. As compliance frameworks evolve and enforcement becomes more stringent, an identity mesh ensures enterprises can prove not just that controls exist, but that they are consistently monitored, automatically validated, and continuously enforced. This significantly reduces audit fatigue, accelerates certification timelines, and strengthens overall regulatory readiness. Identity Mesh improves compliance by:
- Creating a single governance layer
- Centralising policy enforcement
- Providing enterprise-wide identity logs
- Enabling faster investigations
- Simplifying certification and access reviews
Auditors benefit from a consolidated identity view instead of 20+ application-level reports.
Key Elements of an Identity Mesh Strategy
Below are essential building blocks enterprises should include:
1. Identity API Layer
- Standardised APIs for provisioning, authentication, attestation, and governance.
2. Policy-as-Code Engine
- Declarative, reusable policy libraries.
- Automatically enforce access controls across all applications.
3. Real-Time Identity Graph
- Visual representation of user, machine, and workload relationships.
- Useful for threat detection and governance.
4. Universal Connector Framework
- Integrates cloud, on-prem systems, SaaS apps, and DevOps pipelines.
5. AI-Powered Identity Intelligence
- Continuous monitoring
- Risk scoring
- Automated incident response
6. Decentralised Enforcement Points
- Access decisions occur at the closest node: API gateway, application, microservice, or cloud-native cluster.
Conclusion: Identity Mesh Is No Longer Optional
Enterprises can no longer rely on monolithic IAM architectures that were built for predictable, centralised networks. With the rapid growth of cloud adoption, remote work, machine identities, and AI-enhanced cyberattacks, identity has become the enterprise’s most valuable and most targeted asset.
An Identity Mesh Strategy equips organisations with the agility, visibility, and intelligence needed to manage identity at scale. It empowers security teams to modernise IAM without ripping out legacy systems, reduce operational burden, and build a resilient, Zero Trust–driven security posture.
For enterprises preparing for the next decade of digital transformation-