INTRODUCTION
From aerospace to agriculture, the world is being mirrored in real-time by its digital counterpart: the Digital Twin. By simulating the physical world, digital twins promise extraordinary predictive power and efficiency. But beneath this innovation lies a critical question: Are we building the future, or exposing ourselves to a new dimension of cybersecurity threats?
Let’s unravel the double-edged sword of digital twin technology, where seamless simulation collides with the chilling reality of cyber vulnerability.
WHAT IS A DIGITAL TWIN?
A Digital Twin is a real-time virtual replica of a physical object, system, or process, powered by data from sensors, IoT devices, machine learning algorithms, and cloud computing
Unlike a static model, a digital twin is dynamic; it evolves and updates continuously based on live inputs from its real-world counterpart. This enables organisations to simulate, predict, and optimise operations in real-time.
Digital twins are utilised across various industries. In aerospace, a digital twin of a jet engine monitors wear and tear to predict maintenance needs. In healthcare, digital replicas of organs are used to test treatment outcomes. In urban planning, entire cities are digitally mirrored to analyse traffic, utilities, and environmental impacts.
What sets digital twins apart is their ability to mirror behaviour and respond to changes, enabling proactive decision-making and reduced operational risk. As AI and IoT become more advanced, digital twins are no longer futuristic; they’re becoming foundational to Industry 4.0 and beyond.
THE REAL-WORLD IMPACT OF DIGITAL TWINS

1. Manufacturing & Industry 4.0
Digital twins in manufacturing reduce downtime by 30–50%, according to Deloitte, by predicting equipment failure before it happens.
2. Healthcare
Companies like Siemens are creating digital twins of the human heart, enabling personalised treatment simulation and planning for high-risk patients.
3. Smart Cities
Cities like Singapore use digital twins to simulate traffic, waste management, and public utilities to optimise performance in real time.
4. Aerospace
NASA was one of the pioneers of digital twins, using them for space mission planning and fault detection systems on spacecraft.
THE PROBLEM: A SECURITY NIGHTMARE IN THE MAKING?
With continuous real-time data ingestion, integration with cloud platforms, and remote-control capabilities, digital twins are gold mines for cybercriminals.
- IoT Vulnerabilities: Most digital twins depend on IoT devices, which are notoriously insecure and lack endpoint protection.
- Data Breaches: Sensitive telemetry and behavioural data can be intercepted and used for espionage or sabotage.
- Control Hijacking: Digital twins connected to control systems (like HVAC or power grids) can be hijacked to manipulate the physical system.
According to Gartner, by 2027, 70% of organisations implementing digital twins will expose themselves to significant cyber risk without proper identity access governance.
IAM: THE UNSUNG HERO IN SECURING DIGITAL TWINS
In a hyper-connected simulation environment, Identity and Access Management (IAM) is your first line of defence.
IAM ensures that only the right people and machines have the right access at the right time, a crucial layer of control in digital twin ecosystems.
🔐 How IAM Protects Digital Twins:

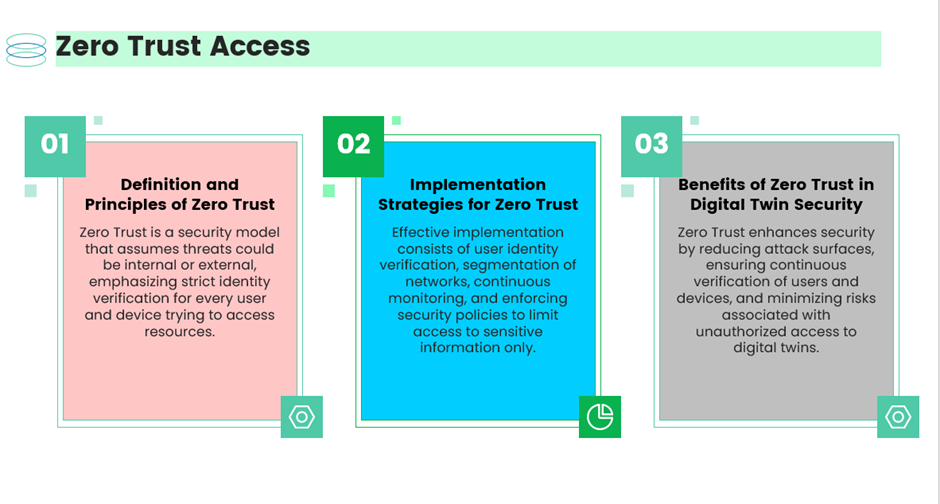
- Zero Trust Access: Prevents lateral movement by verifying every access request based on context, device health, and behaviour.
- Multi-Factor Authentication (MFA): Adds an extra layer of authentication to prevent unauthorised control of twin environments.
- Role-Based Access Control (RBAC): Ensures only authorised users or applications can perform sensitive actions like overriding real-world controls.
- Privileged Access Management (PAM): Controls and audits the superuser accounts which hold the keys to simulation frameworks.
REAL-WORLD INCIDENT: A WARNING FROM THE TRENCHES
In 2023, a European smart manufacturing company suffered a cyberattack where its digital twin environment was accessed via an exploited IoT vulnerability. The attacker simulated faulty behaviour in the digital twin, leading operators to take incorrect physical actions, causing a production line failure and a $2.5M loss.
The post-mortem revealed a lack of IAM policies governing machine-to-machine communication, and no real-time anomaly detection was built into access logs.
IAM BEST PRACTICES FOR DIGITAL TWIN SECURITY

As digital twins become deeply integrated into operational ecosystems, ranging from industrial IoT networks to smart cities and healthcare systems, traditional perimeter-based security is no longer sufficient. Identity and Access Management (IAM) must evolve to govern not just human users but machines, APIs, sensors, bots, and digital services that constantly interact within the digital twin environment.
🔑 1. Implement Zero Trust Architecture
In a digital twin ecosystem, trust should never be assumed. Every access request, from a sensor data stream to a maintenance engineer’s login, must be authenticated, authorised, and continuously validated. Zero Trust helps prevent lateral movement in case of a breach.
🔒 2. Use Strong, Context-Aware MFA
Go beyond basic two-factor authentication. Enforce adaptive MFA policies that consider geolocation, time of day, device fingerprinting, and behavioural biometrics before granting access to simulation dashboards or control interfaces.
🤖 3. Manage Machine Identities with Equal Rigour
Treat machines as first-class citizens. Assign unique credentials to each device, regularly rotate secrets, and use certificate-based authentication to secure communication between components like digital twins, control systems, and cloud platforms.
📊 4. Real-Time Auditing and Behavioural Monitoring
Log every access and change in real time. Feed these logs into SIEM systems that use AI to detect abnormal access patterns, like a twin trying to execute a command outside its behavioural norm.
📁 5. Define Fine-Grained RBAC & ABAC Policies
Enforce least privilege. Create role- or attribute-based access control policies that prevent over-permissioned access, especially for contractors or third-party integrations that interact with twin APIs.
THE ETHICAL ANGLE: WHO OWNS THE DIGITAL SELF?
As digital twins begin representing humans, through health models, behavioural simulations, and even digital personas for deceased individuals, questions of consent, data ownership, and digital legacy emerge.
- Can a digital twin outlive its subject?
- Who controls the decisions made based on your digital twin after death?
IAM frameworks are now evolving to include digital consent policies and post-mortem access governance, becoming the gatekeeper of digital identity in an era of simulated immortality.

WHAT’S NEXT: SECURING FUTURE OF SIMULATION
The future of digital twins is exhilarating, but only if the cybersecurity spine keeps pace with innovation.
Identity-first security, governed by modern IAM platforms, is the only way to ensure digital twin ecosystems are resilient, ethical, and secure.
Expect IAM to evolve toward:
- AI-augmented decision engines
- Automated response to anomalous access patterns
- Integration with quantum-proof authentication in future environments
CONCLUSION: INNOVATION WITHOUT SECURITY IS A RISK MULTIPLIER
As we step into a future where simulations influence decisions, outcomes, and even lives, digital twins will be as critical as their physical counterparts. But every innovation comes with a flip side.

Without robust Identity and Access Management, the same technology that enables predictive precision may also unleash chaotic breach scenarios.
The call is clear: If we’re simulating the world, we need security that’s just as intelligent. And it begins with IAM.





