How Deepfakes Challenge Identity Verification
I’ve spent decades helping organisations build systems designed to protect trust; trust between employees and enterprises, customers and platforms, partners and ecosystems. And if there’s one shift that has fundamentally changed how we must think about identity verification, it is this:
We can no longer assume that what looks real is real
Deepfakes have quietly moved identity risk into a new phase. Not theoretical. Not experimental. Operational. Scalable. And dangerously effective when organisations rely on outdated verification assumptions.
This is not a technology problem alone.
It is a Leadership Challenge.
I. Why Deepfakes Are a Different Kind of Threat
Fraud has always existed. Identity fraud is not new.
What is new is the speed, realism, and accessibility of deepfake technology.
Deepfakes use AI models to generate:
- hyper-realistic faces,
- synthetic voices,
- manipulated videos,
- convincing document imagery.

And crucially, they are no longer limited to well-funded attackers.
Today, deepfake creation:
- requires minimal technical expertise,
- is widely available through open-source tools,
- can be executed at scale,
- and is constantly improving in realism.
This changes the economics of identity fraud completely.
II. The Old Assumption That Is Now Broken
Traditional identity verification relied on a simple assumption:
“If someone can present the right document or biometric, they must be legitimate.”
Deepfakes break this assumption.
They allow attackers to:
- present convincing facial biometrics,
- pass basic liveness checks,
- impersonate real individuals during video verification,
- manipulate onboarding workflows designed for trust, not deception.
This is why identity verification is no longer about validation.
It is about confidence under uncertainty.
III. Where Deepfakes Hit Identity Verification the Hardest
Deepfakes do not attack all identity systems equally.
They exploit specific weak points.

1. Remote Onboarding and Digital KYC
Remote onboarding is now standard across industries:
- financial services,
- healthcare,
- gig platforms,
- SaaS,
- enterprise access provisioning.
Deepfakes thrive here because:
- human oversight is limited,
- verification relies heavily on visual and audio cues,
- speed is prioritised over scrutiny.
Real-world pattern:
Attackers use deepfake videos to impersonate real individuals during video-based KYC, often combined with stolen or synthetic documents.
2. Biometric-Only Verification Models
Biometrics were once considered the gold standard.
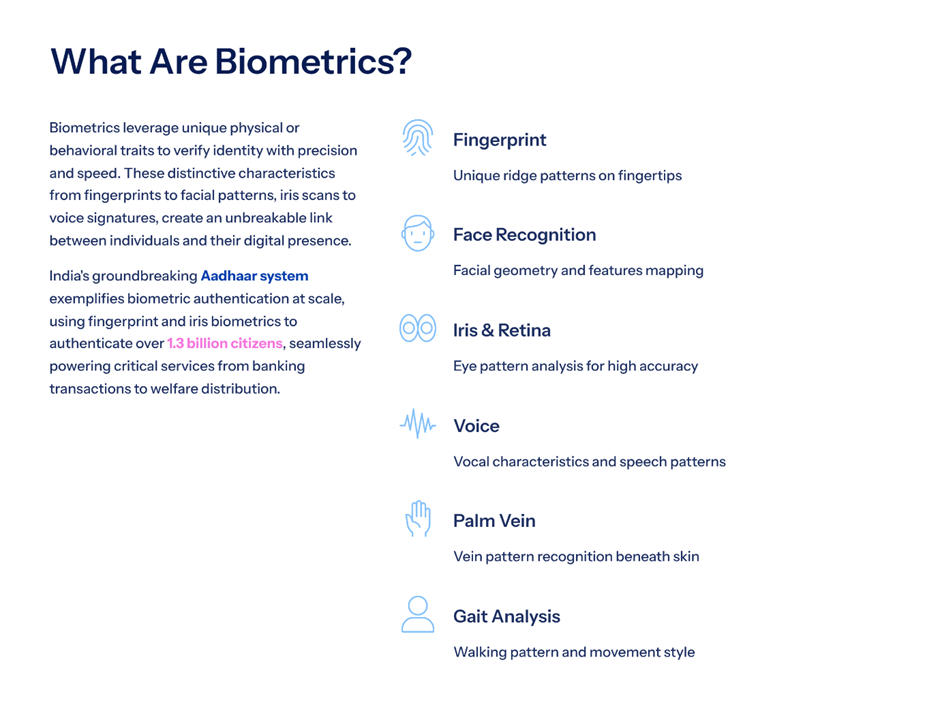
But deepfakes expose a critical flaw:
- A biometric proves similarity, not authenticity.
If a system relies solely on:
- face recognition,
- voice recognition,
- static liveness checks,
It becomes vulnerable to AI-generated inputs designed specifically to bypass those checks.
3. Helpdesk and Assisted Verification

Many breaches still begin with social engineering.
Deepfakes amplify this by enabling:
- real-time voice impersonation of executives,
- video calls posing as legitimate employees,
- convincing urgency narratives.
These attacks bypass controls not through technology, but through human trust.
IV. Why Traditional Controls Are Struggling
Let’s be honest about why many identity programs are unprepared.
Common weaknesses I see repeatedly:
- Over-reliance on one-time identity proofing
- Static trust models
- Legacy liveness detection
- Siloed identity signals
- Lack of behavioural monitoring
None of these were designed for adversaries who can generate realism on demand.
Deepfakes don’t break rules.
They play by the rules better than humans do.
V. The Deepfake Problem Is Not Visual; It’s Contextual
One of the most important leadership insights is this:
Deepfakes succeed because identity verification lacks context.
A face on a screen tells you nothing about:
- behavioural consistency,
- device history,
- interaction patterns,
- risk signals over time.
This is why modern identity verification must move beyond “Is this face real?” to: “Does this identity behave like the real person over time?”
VI. How Modern Identity Verification Must Evolve
From a CXO perspective, the response to deepfakes is not panic; it is redesign.
1. Move from One-Time Verification to Continuous Confidence

Identity must be assessed:
- across sessions,
- across devices,
- across behaviours.
Trust should decay over time unless reinforced.
This is foundational to Zero Trust identity.
2. Combine Multiple Identity Signals

No single signal is reliable anymore.
Resilient identity verification combines:
- document authenticity checks,
- advanced liveness detection,
- behavioural biometrics,
- device intelligence,
- contextual risk scoring.
Deepfakes struggle when forced to maintain consistency across multiple dimensions.
3. Treat Liveness Detection as Adaptive, Not Static
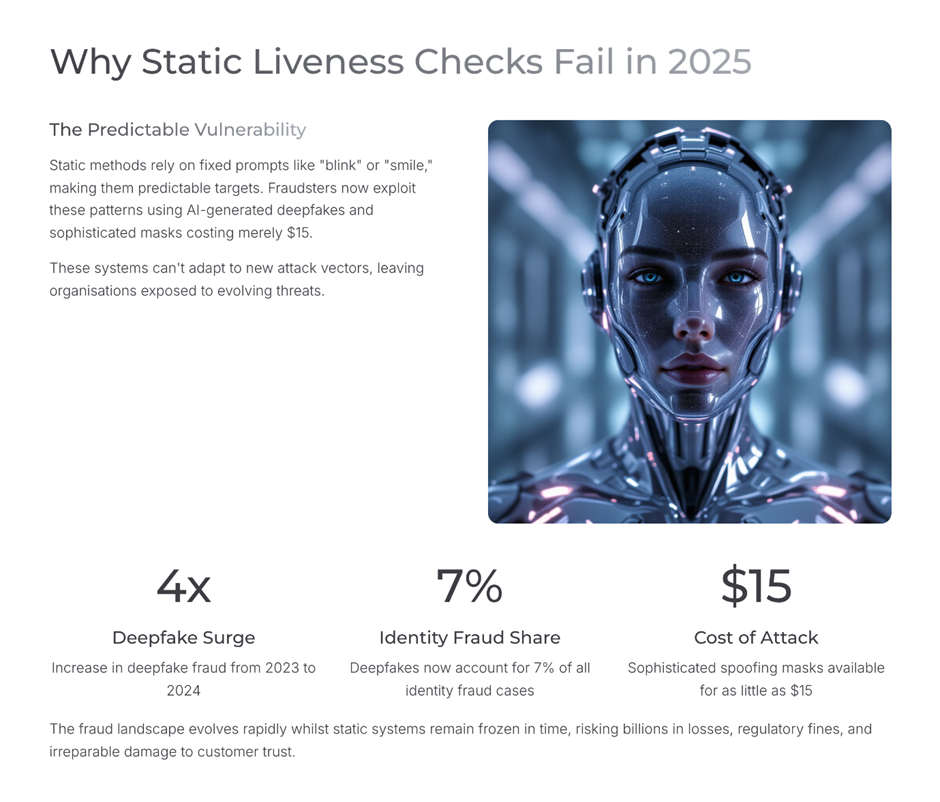
Basic “blink and smile” checks are no longer sufficient.
Modern liveness detection evaluates:
- micro-movements,
- depth perception,
- interaction unpredictability,
- response timing.
And even that must be risk-based, not universal.
4. Introduce Behavioural Identity as a Second Layer
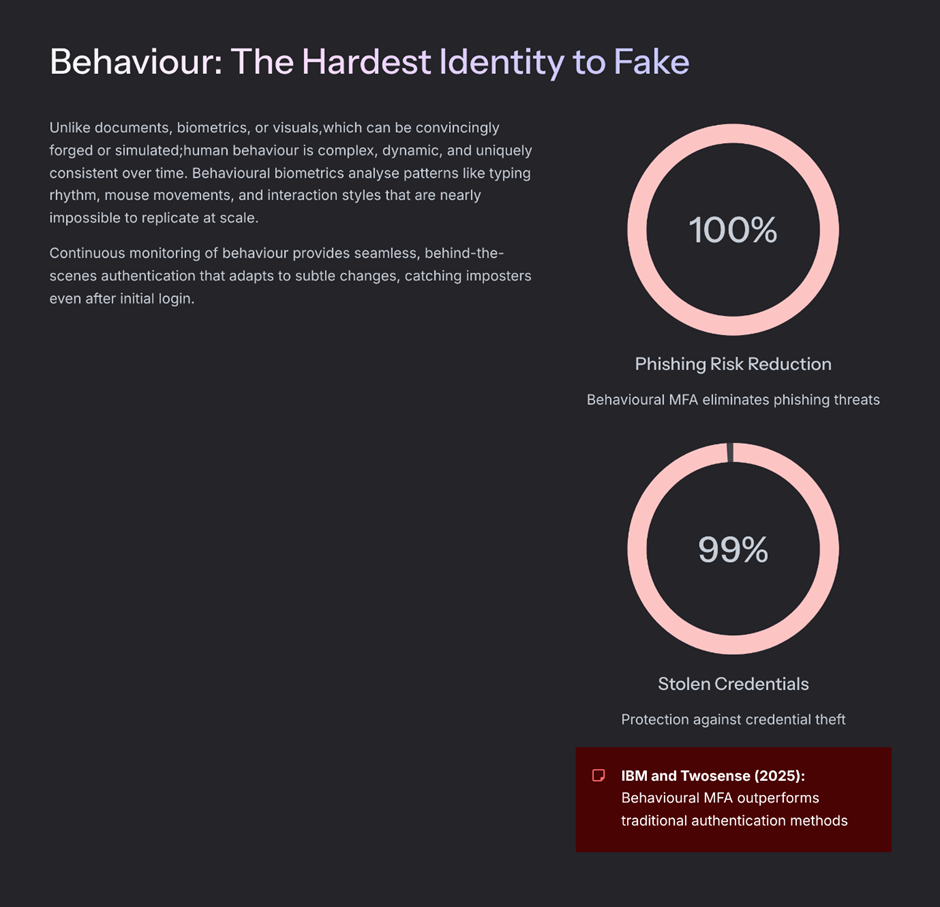
Behaviour is extremely difficult to fake consistently, and that is precisely why it has become such a powerful reinforcement for modern identity verification. While documents, biometrics, and visuals can now be convincingly simulated, sustained human behaviour remains far more resistant to manipulation at scale.
Behavioural identity looks beyond who someone claims to be and observes how they naturally operate over time. This includes:
- typing patterns and rhythm,
- navigation behaviour across applications,
- interaction timing and response cadence,
- habitual device usage and session continuity.
What makes behavioural identity valuable is not any single signal, but the consistency across signals. Deepfakes may pass an initial check, but they struggle to maintain realistic behavioural patterns across sessions, devices, and contexts.
Importantly, behavioural identity is not designed to replace traditional verification methods. It acts as a confidence layer, continuously reinforcing or questioning trust as interactions evolve. When behaviour aligns with historical patterns, systems can reduce friction. When it deviates meaningfully, systems can respond intelligently.
From a leadership perspective, this approach shifts identity verification from a moment in time to an ongoing trust relationship, making impersonation far harder to sustain and far easier to detect early, before damage occurs.
VII. Deepfakes and Zero Trust: The Overlooked Link
Zero Trust architectures often focus on access enforcement.
But deepfakes expose a deeper truth:
Zero Trust fails if identity confidence is weak at entry.
If a deepfake passes initial verification:
- MFA becomes noise,
- access policies enforce the wrong identity,
- monitoring reacts too late.
Identity proofing is not an upstream checkbox.
It is the first Zero Trust control.
VIII. Human Experience Still Matters; Even More Now
There is a dangerous misconception in many organisations that stronger identity verification must automatically translate into more friction for everyone. That belief is not only outdated; it is counterproductive. When security leaders assume that protection requires inconvenience, they design systems that unintentionally train people to work against them.
In reality, identity systems that are resilient to deepfakes behave very differently. They are not loud. They are not intrusive by default. They do not treat every user as a suspect. Instead, they are selectively rigorous.
Deepfake-resilient identity systems are designed to:
- increase friction only when risk genuinely rises,
- remain largely invisible to legitimate users going about their work,
- protect trust without exhausting the very people they are meant to protect.
This balance is not achieved through heavier controls or more frequent challenges. It is achieved through intelligent design; a design that understands context, behaviour, and intent. Systems must learn when to stay out of the way and when to intervene decisively. Anything else creates noise, not security.
When security punishes everyone equally, the outcomes are predictable:
- people become fatigued,
- approvals turn mechanical,
- controls are bypassed “temporarily,”
- and resistance quietly builds.
Fatigue is not apathy. It is a natural response to systems that demand constant attention without offering clarity. Over time, fatigued users stop distinguishing between legitimate safeguards and unnecessary obstacles. That is precisely the environment deepfakes thrive in.
Deepfakes do not succeed solely because they are technologically sophisticated. They succeed because they enter ecosystems where humans are already overloaded, disengaged, and conditioned to comply without thinking. In such environments, realism goes unquestioned, and urgency overrides judgment.
From a leadership perspective, this makes human experience a security control in its own right. Designing identity verification that respects human limits is not a soft consideration; it is a strategic defence. When people remain alert, informed, and supported rather than drained, deepfakes lose one of their greatest advantages: human fatigue.
Protecting identity at scale now requires protecting attention, trust, and judgment as carefully as we protect systems.
IX. Real-World Insight: Where Organisations Get This Wrong
In the field, identity programs fail against deepfakes when:
- AI is bolted on without redesigning workflows,
- verification is treated as compliance, not confidence,
- human experience is ignored,
- leadership delegates identity strategy entirely to tools.

If your identity program assumes “proof once, trust forever,” deepfakes already have a head start.
X. Why This Is a CXO Responsibility
Deepfake-driven identity fraud impacts:
- financial loss,
- regulatory exposure,
- brand reputation,
- customer trust,
- employee confidence.
This makes identity verification:
- a business resilience issue,
- a trust issue,
- a leadership issue.
CXOs must ask:

- How confident are we in the identities we trust today?
- Where does trust decay, and do we notice?
- Are we designing identity for attackers or for reality?
Identity verification can no longer be delegated as a tooling decision.
In a deepfake era, it is a board-level trust conversation.
The Path Forward: Designing for Uncertainty
The future of identity verification is not about certainty.
It is about managing uncertainty intelligently.
That means:
- accepting that visuals can lie,
- designing identity as a system, not a step,
- combining technology with behavioural insight,
- and leading identity conversations at the executive level.
Deepfakes are not the end of trust.
They are a forcing function.
They force us to design identity systems that reflect how the world actually works, not how we wish it did.
Closing Thought from the Field
The most dangerous deepfake is not the one that looks real.
It is the one that fits seamlessly into systems built on outdated trust assumptions.
Identity verification must evolve; not because technology demands it, but because trust does.
And trust, once lost, is far harder to rebuild than to protect.






