Hybrid work isn’t a “pandemic patch” anymore; it’s the operating system of modern business. That shift didn’t just change where people log in. It rewired how identities are created, how access is granted, and how attackers break in. I’ve spent the last few years in the identity trenches, helping teams ship new products without shipping new attack paths. If you’re a CIO or CISO staring down a tangle of SaaS, BYOD, contractors, and shadow automation, this playbook is for you.
The uncomfortable truth: most cloud and workplace incidents aren’t “0-day movie plots.” They’re identity-first compromises, including credential misuse, token replay, session hijack, over-privileged roles, stale service accounts, and those exacerbated by hybrid work. Verizon’s 2024 DBIR puts numbers behind the intuition: the human element factored into 68% of breaches, and vulnerability exploitation surged, while extortion/ransom made up roughly a third of breaches. Translation: identity decisions at the edge (and the speed at which you can correct them) are make-or-break for resilience. Verizon+1
And the dollars hurt. IBM’s latest data show that average breach costs are pushing toward $4.9M–$5.0M globally, with higher costs for regulated industries, capital that could have been used for modernisation or expansion. If your hybrid identity layer is brittle, you’re not just risking downtime; you’re burning runway. IBMTable Media
Below is a pragmatic, identity-first playbook you can start applying this quarter; no hype, just what’s working in real environments.
A.) Hybrid Reality Check: What Changed (and Why IAM Must Lead)
1) Identities now live everywhere.
Employees, contractors, partners, bots, and low-code automations call your APIs from coffee shops, airports, and smart TVs. Microsoft’s 2024 threat analysis shows the vast majority of attack paths terminate in (or pass through) a sensitive user account; identity is the new blast radius. Microsoft+1
2) Attackers log in; they don’t break in.
Recent headline cases, MGM and the Snowflake customer breaches, weren’t magic zero-days; they were identity abuses (helpdesk/social engineering, credential reuse, sessions, weak/no MFA). The Snowflake intrusions, for example, leveraged stolen credentials and instances without MFA enabled to exfiltrate data at scale.
3) Hybrid isn’t going away.
Despite some pressure to return to the office, hybrid remains a competitive advantage for talent and productivity. Multiple datasets show hybrid/remote stabilising at meaningful levels; design for it, don’t fight it. officernd.comMarketWatch
Implication: Your perimeter is your people and your policies. IAM is the control plane of hybrid work.
B.) What the Last 18 Months Taught Us (Real-World Patterns)
- SSO & token trust are only as strong as your support processes.
The MGM incident highlighted how social engineering against help desks cascades into identity compromise. It’s not just your IDP configuration; it’s the people and process around it. ThriveDXUniversity of Hawai’i – West O’ahu
- Third-party cases can ricochet into your environment.
Okta’s 2023 support system incident showed how session tokens inside HAR files became a pivoting point for attackers. Even if the IDP core is fine, adjacent workflows (troubleshooting artefacts, logs, integrations) can become identity landmines. Okta Security+1
- Passwords remain the soft underbelly.
Microsoft’s 2024 defence report emphasises that identity attacks are overwhelmingly password-based. If you still tolerate weak or reused secrets across hybrid estates, you’re sponsoring your adversary’s cloud bill. Microsoft
C.) The Playbook: 12 Moves to Make Hybrid Work Secure (and Usable)

1) Adopt an Identity-First Architecture
- Treat the IDP (and its policies) as your de facto perimeter.
- Centralise authN/authZ for web, SaaS, VPN, and internal apps; eradicate “islands of identity.”
- Enforce modern protocols (OpenID Connect, OAuth 2.1, SCIM) end-to-end.
2) Passwordless & Strong MFA as a Program (Not a Project)
- Go beyond SMS. Favour FIDO2/WebAuthn, device-bound passkeys, and hardware security keys for admins and high-risk roles.
- Use adaptive MFA so low-risk access stays smooth while risky access gets stepped up; security and UX.
3) Continuous Access Evaluation (CAE) & Session Defence
- Revoke tokens in near-real time on device risk change, employment change, or policy violation.
- Shorten session lifetimes for privileged roles; bind tokens to device posture when possible.
4) Make Least-Privilege the Default, Not the Exception
- Replace coarse RBAC with task-based roles and just-in-time elevation.
- Expire temporary privileges automatically; require approvals logged to an immutable ledger.
5) Harden the Helpdesk
- Gate identity-affecting tickets behind out-of-band verification (challenge-response that only the real user can satisfy).
- Don’t let agents reset MFA or issue break-glass accounts without dual control and session recording.
- Train for AI-voice and phone-based social engineering; it’s surging in hospitality and beyond. The Wall Street Journal
6) MFA Everywhere that Matters (Including Vendors)
- Third-party and contractor identities must be subject to the same or stronger MFA/conditional access you apply internally.
- For B2B integrations, use OAuth client credentials with rotation, not long-lived static secrets.
7) Inventory & Govern Non-Human Identities
- Catalogue service accounts, API keys, CI/CD robots, and low-code automations.
- Rotate keys automatically; move to workload identity federation where possible.
- Monitor for drift; non-human sprawl is the shadow IT of 2025.
8) Data-Aware Access
- Tag sensitive data (customer PII, source code, models) and bind access policies to those tags.
- Use conditional access that understands data sensitivity and device risk together.
9) Detect the Identity Kill Chain
- Telemetry you need: sign-in events, consent grants, token anomalies, impossible travel, MFA fatigue, risky OAuth app creation.
- Feed your SIEM/UEBA and tune alerts for identity sequence patterns, not just single events.
10) Automate Access Reviews
- Quarterly spreadsheet attestation doesn’t scale.
- Trigger reviews on org changes (joiners/movers/leavers), new app onboarding, or abnormal privilege usage.
11) Resilience & Recovery for Identity
- Keep an offline “break-glass” plan (documented, tested), separate from your IDP.
- Pre-stage paths to revoke, re-issue, and re-enrol MFA for the entire org within hours.
12) Measure What Matters
- Time to detect identity misuse (goal: hours, not days).
- % workforce on phishing-resistant MFA.
- % non-human identities with automated secret rotation.
- Admin role exposure time (how long someone stays privileged).
Reduction in excessive grants after each review cycle.
D.) Fresh Thinking: Governance Patterns That Move the Needle
1) Consent Guardrails for OAuth/SaaS Sprawl
Move from “allow by default” to “pre-approved, least-scope” OAuth grants. Block risky delegated permissions unless justified and time-boxed. Many Snowflake-adjacent incidents started with overbroad or unmonitored grants, and no MFA on the target. Google CloudCloud Security Alliance
2) “Support Artefact Hygiene”
Ban raw HAR/log uploads to support portals unless scrubbed. If you must collect them, use a redaction proxy that automatically removes tokens and cookies, and store artefacts in a quarantined, time-boxed bucket. Okta’s 2023 support incident made this painfully real. Okta Security
3) Identity Risk as a First-Class SLO
Report to the board not only patch SLA and endpoint health, but identity risk posture: % of sensitive roles on phishing-resistant MFA, % of external identities with CAE, and mean time to revoke compromised sessions.
4) Invert UX vs. Security
Adopt adaptive friction: 95% of your workforce should experience fewer prompts because the 5% of risky events get more checks. This flips the narrative; security that feels faster than insecure competitors.
E.) Field Notes: What Surprised Leadership (and Won Buy-In)
- When we killed passwords for admins, tickets dropped.
Hardware-backed sign-in removed lockout churn, eliminated password resets, and reduced phishing noise. Microsoft’s telemetry showing password-based identity attacks dominate helped make the case. Microsoft - Helpdesk reforms outperformed new tooling.
Dual-control on MFA resets and “call-back to HR-registered number only” cut account-takeover attempts dramatically, directly addressing MGM-style tradecraft. ThriveDX - Automated access reviews paid for themselves.
Removing zombie access reduced SaaS license spend and audit findings. That budget offset funded passkeys and CAE rollout.
F.) Executive Ready: A 90-Day Hybrid IAM Action Plan

Days 0–30: Baseline & Blast-Radius Mapping
- Consolidate sign-in logs from IDP, VPN, and major SaaS into your SIEM.
- Identify top 20 sensitive roles and top 20 sensitive apps.
- Snapshot: % on phishing-resistant MFA, admin session lifetimes, external/vendor identities, and OAuth apps with high-risk scopes.
Days 31–60: Close the Biggest Holes
- Enforce MFA everywhere for human and partner accounts; start passkeys for admins.
- Implement CAE for sensitive roles; trim session lifetimes.
- Quarantine shadow OAuth apps; publish a pre-approved catalogue.
- Deploy helpdesk hardening (dual-control and scripted verification).
Days 61–90: Govern & Automate
- Stand up automated access reviews tied to HRIS events.
- Migrate service accounts to workload identities with rotation.
- Build the offline identity recovery runbook and test it.
Publish an executive dashboard of identity risk SLOs.
G.) Real-World Examples You Can Borrow
Snowflake customer compromises (2024)
- Pattern: credential theft + no MFA → mass data exfiltration.
- Control to borrow: Enforce MFA on all data platforms; CAE and anomaly alerts on large exports; least privilege on data roles. Google CloudCloud Security Alliance
Okta support incident (2023)
- Pattern: session tokens exposed via support artefacts.
- Control to borrow: Redaction by default, short-lived tokens, artefact quarantine, and partner security reviews. Okta Security
MGM/Scattered Spider (2023)
- Pattern: helpdesk social engineering → identity reset → lateral movement.
- Control to borrow: Strict helpdesk verification flows, no single-operator resets, session recording for privileged support actions, phishing-resistant MFA. ThriveDXUniversity of Hawai’i – West O’ahu
Macro insight (DBIR 2024, Microsoft 2024, IBM 2024)
- Pattern: the human element and identity pathways are dominant; breach costs are rising; password-based attacks persist.
- Control to borrow: identity-first Zero Trust, passwordless rollout, human-centred controls. Verizon+1MicrosoftIBM
H.) Budget Reality: Do More with the Same (or Less)

If you need to sequence investments, here’s how to spend last and save first:
- Free / Already Licensed
- Enforce MFA + conditional access you already own in your IDP suite.
- Turn on sign-in risk policies and risky token detections.
- Automate access reviews with native governance features.
- Low Cost, High Yield
- Hardware keys for admins and break-glass workflows.
- Log pipeline normalisation so your SIEM actually “sees” identity patterns.
- Redaction tooling for support artefacts (or at least documented, enforced SOPs).
- Strategic Add-Ons
- Dedicated identity threat detection & response (ITDR).
- Workload identity federation to kill static keys.
- Data security posture management is tightly coupled to IAM.
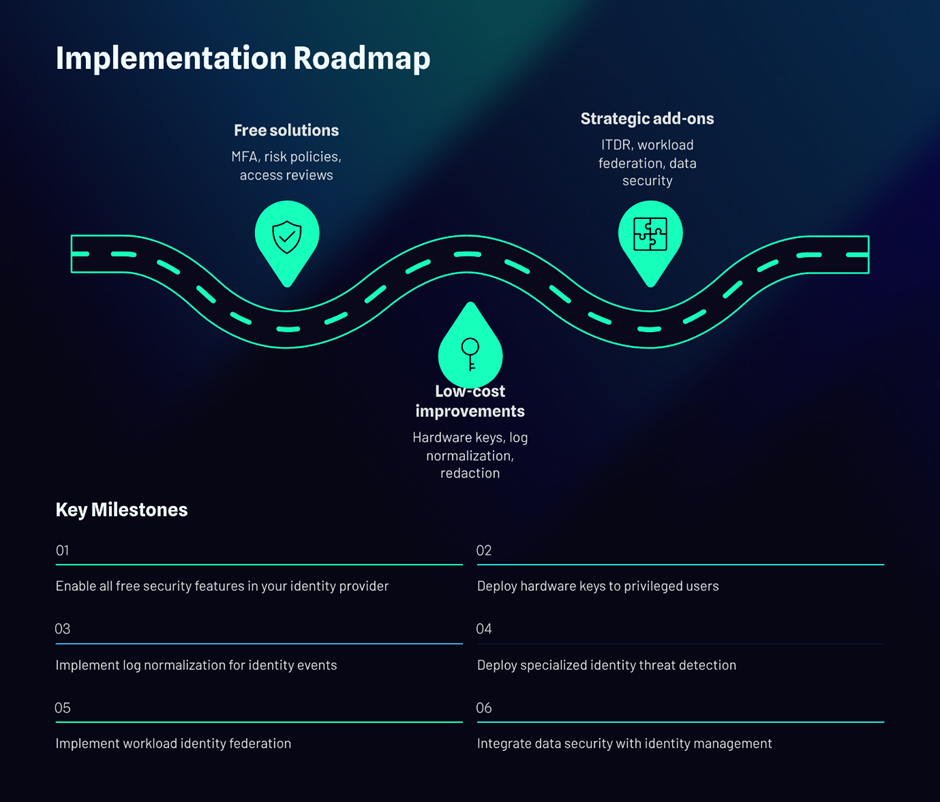
Why this wins: You reduce breach likelihood and operational friction, while freeing license spend hidden in zombie access. The IBM figures on breach costs help justify phase 2–3. IBM
I.) Governance: The Board Understands
Your board doesn’t need an MFA lecture; they need risk movement they can read. Report:
- Exposure: % of sensitive identities on phishing-resistant MFA; number of apps behind SSO; # of third parties without CAE.
- Performance: Mean time to revoke sessions after HR termination; median admin elevation duration.
- Outcome: Reduction in excessive privileges quarter-over-quarter; blocked high-risk OAuth grants; identity-linked incident count.
This reframes IAM from “IT plumbing” to business risk control.
J.) The Surprise Factor: IAM as a Growth Enabler
Here’s the part that often surprises executives: identity improvements don’t just cut risk, they unlock velocity.
- Fewer password resets → fewer lost hours.
- SSO expansion → faster vendor onboarding.
- Just-in-time access → approvals in minutes, not days.
- Automations with workload identities → safer platform engineering, faster releases.
Hybrid work needs speed. Identity makes speed safe.
Your Next Step (and How I Help)
I specialise in making hybrid IAM invisible to good users and impossible for attackers. If you’re a budding or mid-market organisation, you don’t need a 12-month transformation to get safer. You need 90 days of focused change that hardens your identity edges and buys you optionality.
Free posture review (1 hour): We map your top identity risks to quick wins.
90-Day rollout: MFA/CAE + helpdesk hardening + access reviews, measured weekly.
Quarterly governance: board-quality reporting, automated drift checks, and tabletop recovery.
Because hybrid work is here. The only question is whether it’s safe.
Sources (selected)

Verizon DBIR 2024: human element, breach trends. Verizon+1
IBM Cost of a Data Breach 2024/2025; average breach cost trends. IBM+1Table Media
Microsoft Digital Defence Report 2024: identity attack patterns, password-based prevalence, and attack paths. Microsoft+1
MGM / Social Engineering;helpdesk-driven identity compromise. ThriveDXUniversity of Hawai’i – West O’ahu
Snowflake customer incidents 2024: stolen credentials, absent MFA. Google CloudCloud Security Alliance
Okta Support Incident 2023; HAR files & session tokens. Okta Security+1
Hybrid Work Persistence: hybrid share and stability. officernd.comMarketWatch