In today’s hyper-connected digital ecosystem, Identity and Access Management (IAM) is no longer a back-office IT function; it’s a strategic pillar of enterprise security. As cyber threats grow more sophisticated and regulatory demands tighten, organisations must assess and evolve their IAM capabilities. That’s where IAM maturity models come in.
This blog explores what IAM maturity models are, why they matter, how to evaluate your current state, and actionable steps to elevate your enterprise security posture.
A. What Is an IAM Maturity Model?
An IAM maturity model is a structured framework that helps organisations assess the effectiveness, scalability, and security of their identity and access management practices. It provides a roadmap for continuous improvement, guiding enterprises from fragmented access control to fully integrated, intelligent identity governance.
B. The Four Common Levels of IAM Maturity
According to Zluri’s 2025 IAM Maturity Guide, most models follow a four-tier structure:
| Level | Description |
| Level 1: Ad-Hoc | IAM practices are inconsistent, manual, and reactive. No formal policies exist. |
| Level 2: Basic | Some IAM tools are in place, but processes are siloed and lack automation. |
| Level 3: Defined | IAM is standardised across departments with role-based access and compliance controls. |
| Level 4: Optimised | IAM is fully automated, AI-driven, and aligned with zero-trust and business goals. |
C. Why IAM Maturity Matters for Enterprise Security
1. Reduces Risk of Breaches
According to IBM’s 2024 Cost of a Data Breach Report, identity-related breaches cost organisations an average of $4.45 million. Mature IAM systems reduce this risk by enforcing least-privilege access, multi-factor authentication (MFA), and real-time anomaly detection.
2. Ensures Regulatory Compliance
IAM maturity is critical for meeting standards like GDPR, HIPAA, and India’s Personal Data Protection Bill. Mature IAM systems offer audit trails, automated access reviews, and policy enforcement; all essential for compliance.
3. Improves Operational Efficiency
Organisations with optimised IAM save time and money.
A 2023 Gartner study found that automated IAM systems reduce IT helpdesk costs by up to 40%, primarily by eliminating manual provisioning and password resets.
D. How to Evaluate Your IAM Maturity

✅ Step 1: Conduct a Maturity Assessment
Use a structured assessment tool to evaluate your IAM capabilities across key domains:
- Identity Lifecycle Management

- Authentication & Authorization


- Access Governance

- Privileged Access Management (PAM)

- Monitoring & Analytics


✅ Step 2: Benchmark Against Industry Standards
Compare your results with industry benchmarks. For example, Security Scorecard’s 2025 IAM Best Practices recommend:
- Passwordless authentication

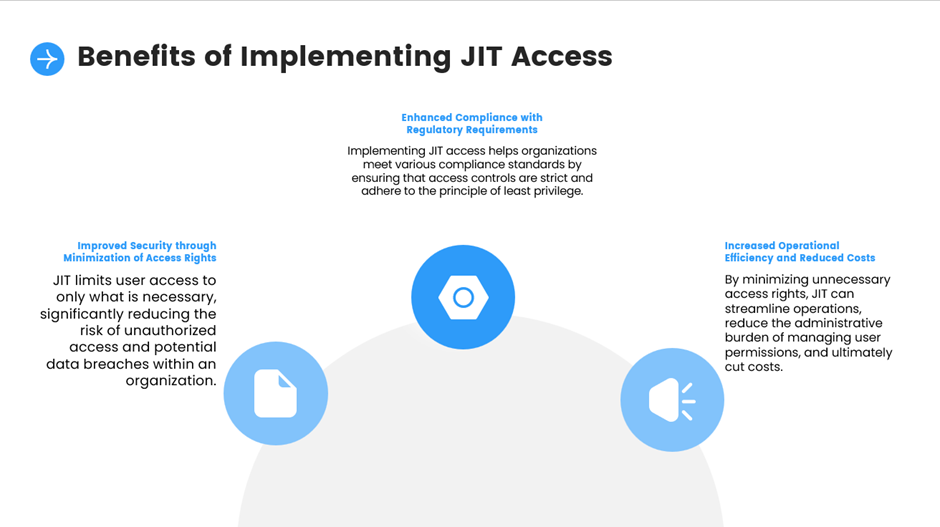
- Just-in-time (JIT) access provisioning
- Continuous identity threat detection

✅ Step 3: Identify Gaps and Prioritise Improvements
Focus on areas with the highest risk or business impact. For instance, if your access reviews are manual and infrequent, prioritise automation and policy enforcement.

E. Key Components of a Mature IAM Program

🔐 1. Identity Lifecycle Automation
From onboarding to offboarding, automate user provisioning and deprovisioning to reduce human error and insider threats.
🔐 2. Multi-Factor Authentication (MFA)
Implement MFA across all user types; employees, vendors, and APIs. According to Microsoft, MFA blocks 99.9% of account compromise attacks.
🔐 3. Role-Based and Attribute-Based Access Control (RBAC/ABAC)
Use RBAC for standard roles and ABAC for dynamic, context-aware access decisions.
🔐 4. Privileged Access Management (PAM)
Secure admin accounts with session recording, time-bound access, and approval workflows.
🔐 5. Identity Threat Detection and Response (ITDR)
Use AI and machine learning to detect unusual behaviour, such as impossible travel or access spikes.
F. IAM in the Era of Zero Trust and Cloud
Modern IAM must align with Zero Trust Architecture (ZTA) and cloud-native environments. This means:
- Continuous verification of user identity and device health
- Context-aware access policies
- Federated identity management across SaaS, IaaS, and on-prem systems
According to Forrester, Zero Trust adoption is expected to reach 90% of enterprises by 2026, and IAM is the foundation of that shift.
G. Case Study: How a Leading Indian Fintech Transformed Security with IAM Maturity
In 2023, a prominent Indian fintech company embarked on a mission to overhaul its identity and access management (IAM) infrastructure. Facing increasing regulatory pressure, rising cyber threats, and operational inefficiencies, the organisation recognised that its existing IAM framework, classified at Level 2 (Basic) on the IAM maturity scale, was no longer sufficient to support its growth or safeguard its digital assets.
At Level 2, the company had implemented some IAM tools, but processes were largely manual, siloed, and reactive. Access provisioning was inconsistent, onboarding was slow, and privileged accounts were not adequately monitored. These gaps not only posed security risks but also hindered compliance with evolving regulations such as the Reserve Bank of India (RBI) cybersecurity guidelines and the General Data Protection Regulation (GDPR) for its European operations.
To address these challenges, the company launched a comprehensive IAM maturity roadmap to reach Level 4 (Optimised) within 18 months.
This roadmap included:
- Automating identity lifecycle management to streamline onboarding and offboarding.
- Implementing multi-factor authentication (MFA) and single sign-on (SSO) across all internal and customer-facing applications.
- Deploying role-based access control (RBAC) and just-in-time (JIT) provisioning to enforce least-privilege access.
- Integrating IAM with HR systems and ITSM tools for seamless provisioning and audit readiness.
- Adopting AI-driven behavioural analytics to detect and respond to identity-based threats in real time.
The transformation was not without its challenges. It required cross-functional collaboration between IT, HR, compliance, and security teams. The company also invested in employee training to ensure smooth adoption of new authentication protocols and access policies.
However, the results were nothing short of remarkable:
- 💰 $500,000 in annual cost savings were realised through reduced IT helpdesk tickets, faster provisioning, and fewer security incidents.
- 🔐 Access-related incidents dropped by 80%, thanks to real-time monitoring and automated access controls.
- 📜 The company achieved full compliance with RBI and GDPR, passing audits with zero major findings.
- 🚀 Employee onboarding time improved by 60%, enhancing productivity and reducing time-to-value for new hires.
Beyond the numbers, the company also gained greater agility and resilience. With a mature IAM framework in place, it could confidently scale operations, onboard partners, and launch new digital services without compromising security.
This case study underscores a powerful truth: IAM maturity is not just a technical upgrade; it’s a strategic enabler. For fintechs navigating complex regulatory landscapes and digital transformation, investing in IAM maturity can unlock significant business value, reduce risk, and build long-term trust with customers and stakeholders.
H. Best Practices to Improve IAM Maturity
| Action | Impact |
| Implement SSO and MFA | Enhances security and user experience |
| Automate provisioning | Reduces IT workload and errors |
| Conduct quarterly access reviews | Ensures compliance and least privilege |
| Integrate IAM with SIEM tools | Enables real-time threat detection |
| Train employees on IAM policies | Builds a security-first culture |
🧩 Choosing the right Identity and Access Management (IAM) solution in 2025 is no longer just a technical decision; it’s a strategic move that can define your organisation’s security posture, operational efficiency, and digital agility. With cyber threats growing more sophisticated and hybrid work environments becoming the norm, businesses must adopt IAM platforms that are not only secure but also scalable, intelligent, and user-centric.
🌐 1. Scalability for Hybrid and Multi-Cloud Environments
Modern enterprises operate across on-premises, cloud, and hybrid infrastructures, often juggling multiple SaaS applications and remote endpoints. A robust IAM solution must scale effortlessly across these environments, ensuring consistent identity governance and access control. Whether you’re onboarding new employees, integrating third-party vendors, or expanding globally, your IAM platform should support dynamic provisioning, federated identity management, and cross-platform compatibility without compromising performance.
🤖 2. AI and Analytics for Threat Detection
IAM is no longer just about who gets access; it’s about how, when, and why. Leading IAM platforms now incorporate AI and machine learning to detect anomalies, flag suspicious behaviour, and enforce adaptive authentication in real time. According to SentinelOne, 89% of organisations experienced identity-based attacks, and 80% believe that better IAM tools could have prevented them. AI-driven IAM helps mitigate these risks by continuously learning from user behaviour and adjusting access policies accordingly.
🔗 3. Seamless Integration with HR, ITSM, and Security Tools
An effective IAM solution should act as the central nervous system of your IT ecosystem. That means integrating smoothly with HR systems (like Workday or SAP) for automated onboarding/offboarding, IT service management tools (like ServiceNow) for access requests and approvals, and SIEM/SOAR platforms for real-time threat response. This level of integration ensures end-to-end visibility, reduces manual errors, and accelerates compliance reporting.
🧑💻 4. User-Friendly Interfaces for Admins and End-Users
Security shouldn’t come at the cost of usability. The best IAM platforms offer intuitive dashboards for administrators to manage roles, policies, and audits, while also providing frictionless experiences for end-users through features like Single Sign-On (SSO), passwordless authentication, and self-service portals. A user-centric design not only boosts productivity but also encourages adoption across departments.
I. Top IAM Vendors to Watch in 2025
Several vendors are leading the IAM space with innovative, enterprise-ready solutions:
| Vendor | Strengths |
| Okta | Cloud-native, app-focused IAM with 7,000+ integrations |
| Microsoft Entra | Deep integration with the Microsoft ecosystem, strong hybrid deployment options |
| Ping Identity | API-first, enterprise-grade IAM with advanced orchestration |
| ForgeRock | Comprehensive identity governance and lifecycle management |
| Saviynt | Cloud-native IGA with strong compliance and analytics capabilities |
These platforms offer varying strengths in scalability, governance, and integration, so the right choice depends on your organisation’s size, industry, and security goals.
Choosing the right IAM solution is about more than ticking boxes; it’s about future-proofing your enterprise. With the right platform, you can reduce risk, streamline operations, and empower your workforce with secure, seamless access.
J. Conclusion: IAM Maturity Is a journey, not a Destination
IAM maturity isn’t a one-time project; it’s a continuous evolution. As your organisation grows and threats evolve, so must your identity strategy. By utilising IAM maturity models, you gain a clear roadmap to enhance security, improve compliance, and foster business agility.
Whether you’re just starting or optimising an existing program, investing in IAM maturity is one of the smartest moves you can make in today’s digital-first world.

📩 Need help assessing your IAM maturity or building a roadmap? Let’s connect and explore how to future-proof your enterprise security.





