Introduction
When your business runs online, a DDoS attack can take everything down-your website, your services, and your customers’ trust, simply everything quintessential for you, all blown out in the blink of an eye. These attacks aim to disrupt the normal functioning of websites, applications, or entire networks by overwhelming them with a flood of internet traffic. The consequences can be severe, ranging from financial losses to reputational damage.
This blog delves into the intricacies of DDoS attacks, exploring their types, recent trends, impacts, and, most importantly, how organisations can defend against them effectively
1. What is a DDoS Attack?

A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. Unlike a Denial of Service (DoS) attack, which typically uses a single computer and internet connection, a DDoS attack utilises multiple compromised computer systems as sources of traffic. These systems can include computers and other networked resources such as IoT devices.
2. Types of DDoS Attacks
Understanding the various types of DDoS attacks is crucial for implementing effective defense mechanisms. The primary categories include:
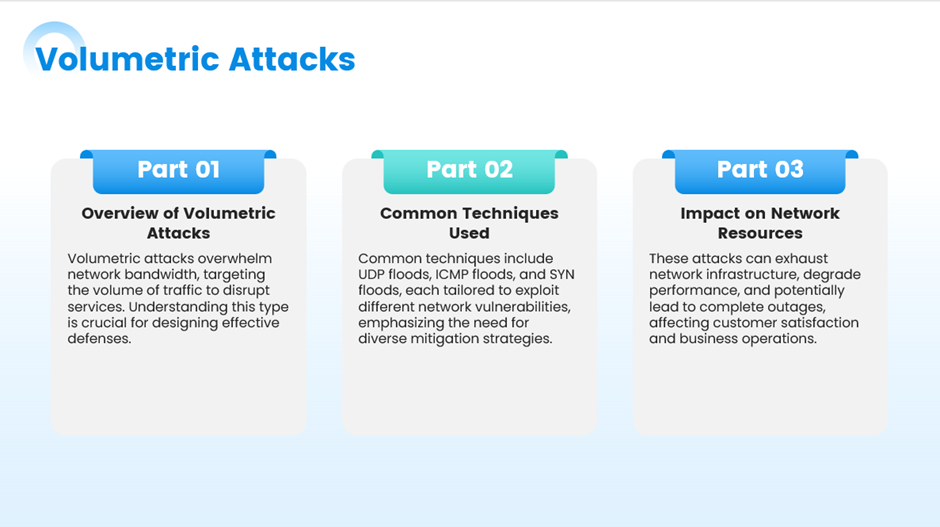
i. Volumetric Attacks
These attacks aim to saturate the bandwidth of the targeted site. They involve massive amounts of data sent to the target, consuming all available bandwidth and rendering the service inaccessible.
Examples:
- UDP floods
- ICMP floods
- DNS amplification attacks
ii. Protocol Attacks
Protocol attacks exploit weaknesses in the protocol stack to consume server resources or intermediate communication equipment, such as firewalls and load balancers.
Examples:
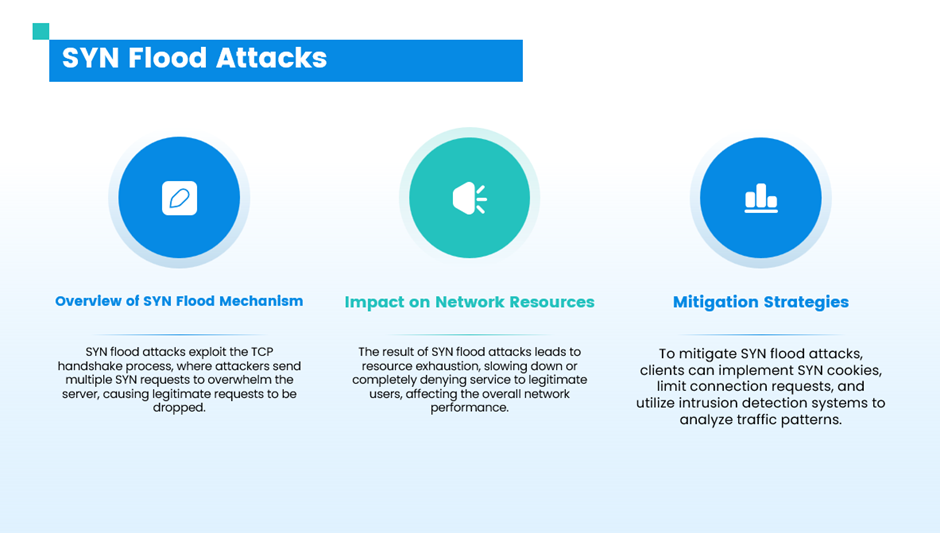
- SYN floods
- Ping of Death
- Smurf DDoS
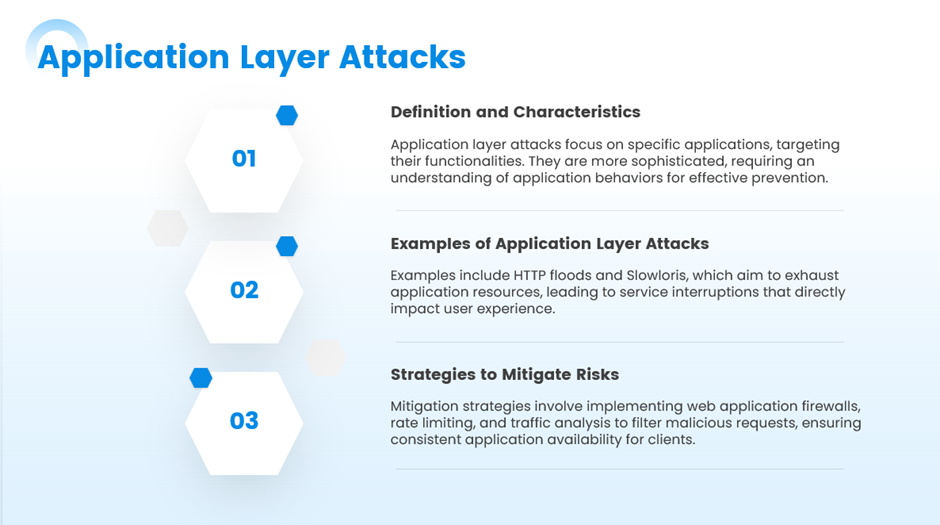
iii. Application Layer Attacks
These attacks target the application layer (Layer 7) of the OSI model, focusing on specific applications or services to exhaust resources.
Examples:
- HTTP floods
- Slowloris
- Zero-day attacks
3. Recent Trends in DDoS Attacks
The Cyber Sabre Between India and Pakistan: A Hacktivist Skirmish Shadowing Hostilities
In the digital age, warfare has transcended traditional battlefields, finding new arenas in cyberspace. The recent tensions between India and Pakistan have illuminated this shift, with hacktivist groups from both nations engaging in a cyber skirmish that paralleled physical hostilities.
A Prelude to Digital Conflict
The catalyst for this cyber confrontation was the tragic terrorist attack in Pahalgam on April 22, 2025. In response, India launched “Operation Sindoor” on May 7, targeting terrorist infrastructures across the border. However, even before the first physical retaliation, cyberspace had already become a battleground. Hacktivist groups initiated cyberattacks, including Distributed Denial of Service (DDoS) assaults, signalling the onset of a digital conflict that would escalate alongside traditional military actions.
The Surge of Cyber Offensives
Between May 7 and May 10, over 650 coordinated cyberattacks targeted India’s critical infrastructure. These attacks, attributed to Pakistan-aligned state and non-state actors, aimed to disrupt essential services and exert geopolitical pressure. The India Meteorological Department (IMD) also reported suspicious access attempts traced to Pakistan and Afghanistan, prompting the implementation of enhanced cybersecurity measures.
Hacktivist Groups and Their Tactics
More than 40 hacktivist groups, including Keymous+, AnonSec, Nation of Saviors, and Electronic Army Special Forces, coordinated cyberattacks against India. Their tactics ranged from DDoS attacks to website defacements, targeting government portals, healthcare infrastructure, and critical industries. While many of these attacks were more symbolic than damaging, they highlighted the increasing role of hacktivists in geopolitical conflicts.
India’s Cyber Counteroffensive
In retaliation, pro-India hacker groups such as the Indian Cyber Force (ICF), Kerala Cyber Xtractors, and Indian Cyber Defender launched counterattacks. These groups breached Pakistani government and institutional systems, including surveillance networks and bank databases, employing tactics like ransomware and social engineering to neutralize Pakistani systems and expose sensitive data .
The Reality Behind the Numbers
Despite claims of over 1.5 million cyberattacks launched by Pakistan-allied hackers on Indian websites, only 150 were successful. This disparity underscores the importance of robust cybersecurity measures and the resilience of India’s digital infrastructure.
The Road Ahead
The cyber skirmish between India and Pakistan serves as a stark reminder of the evolving nature of warfare. As nations continue to digitise, the importance of cybersecurity cannot be overstated. Investing in cyber defense capabilities, fostering public-private partnerships, and training cybersecurity professionals are essential steps to safeguard national interests in this new era of digital conflict.
Note: This article is based on information available as of May 27, 2025. For the most current updates, please refer to official sources and recent news reports.
Sources:


The landscape of DDoS attacks is continually evolving, with attackers employing more sophisticated methods. Recent reports indicate a significant surge in the frequency and complexity of these attacks.
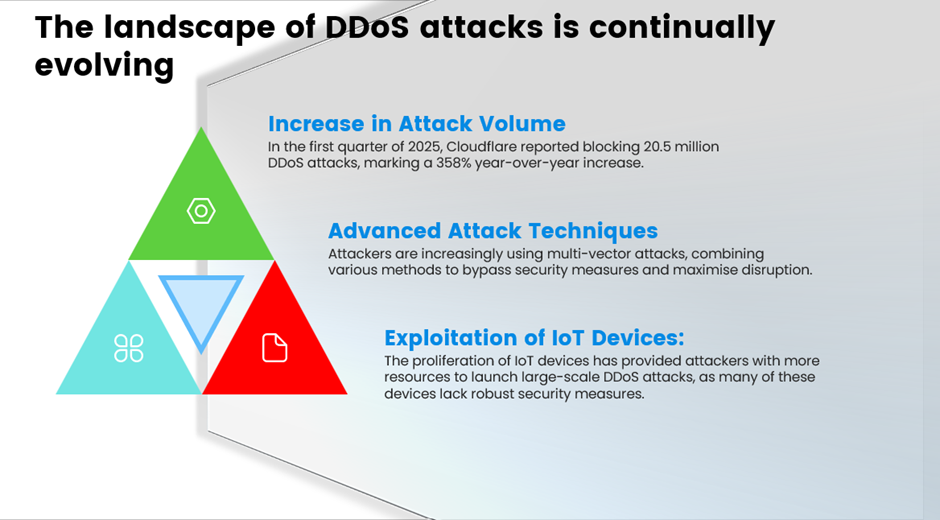
- Increase in Attack Volume: In the first quarter of 2025, Cloudflare reported blocking 20.5 million DDoS attacks, marking a 358% year-over-year increase.
- Advanced Attack Techniques: Attackers are increasingly using multi-vector attacks, combining various methods to bypass security measures and maximise disruption.
- Exploitation of IoT Devices: The proliferation of IoT devices has provided attackers with more resources to launch large-scale DDoS attacks, as many of these devices lack robust security measures.
4. Impact of DDoS Attacks
The consequences of DDoS attacks can be devastating for organizations:
- Financial Losses: Downtime can lead to significant revenue loss, especially for e-commerce platforms and financial institutions.
- Reputational Damage: Frequent or prolonged outages can erode customer trust and damage the organization’s reputation.
- Operational Disruption: Internal systems and operations can be severely affected, leading to decreased productivity.
- Security Breaches: DDoS attacks can serve as a smokescreen for other malicious activities, such as data breaches.
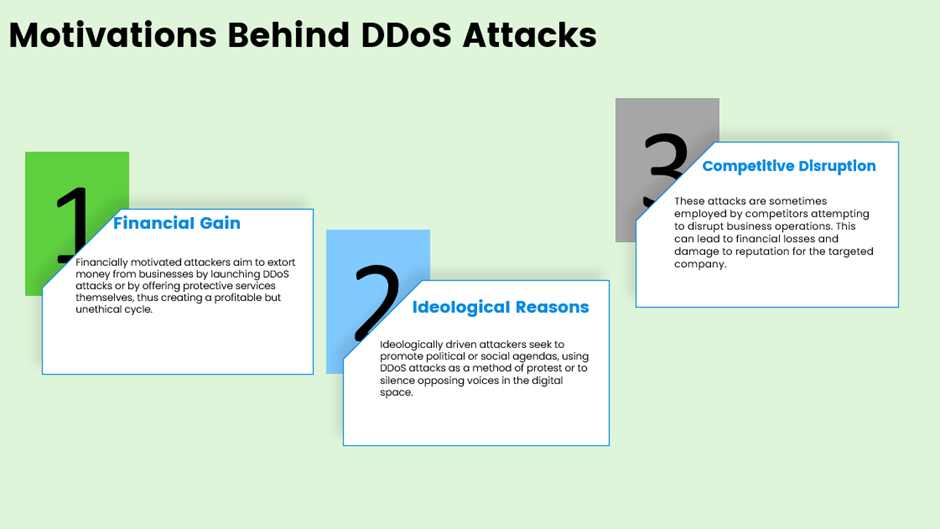
5. Mitigation Strategies

Defending against DDoS attacks requires a multi-faceted approach:
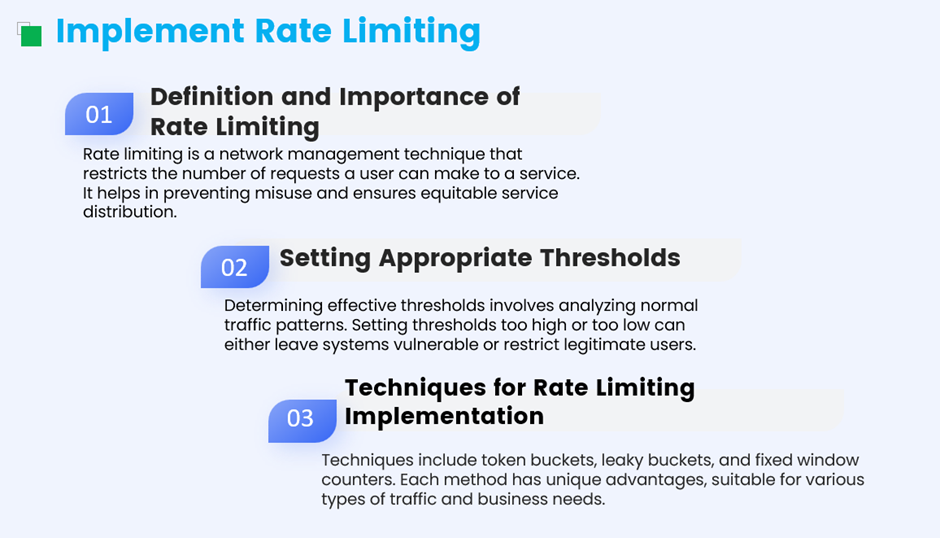
i. Implement Rate Limiting
Rate limiting controls the number of requests a user can make to a server within a specific time frame, helping to prevent overwhelming traffic.
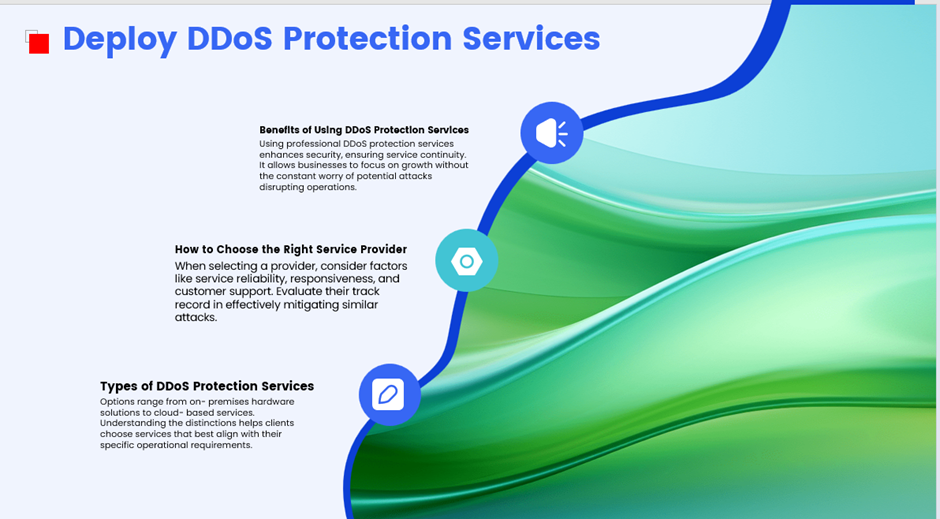
ii. Deploy DDoS Protection Services
Utilize services that specialize in detecting and mitigating DDoS attacks. These services often employ AI and machine learning to identify and respond to threats in real-time.
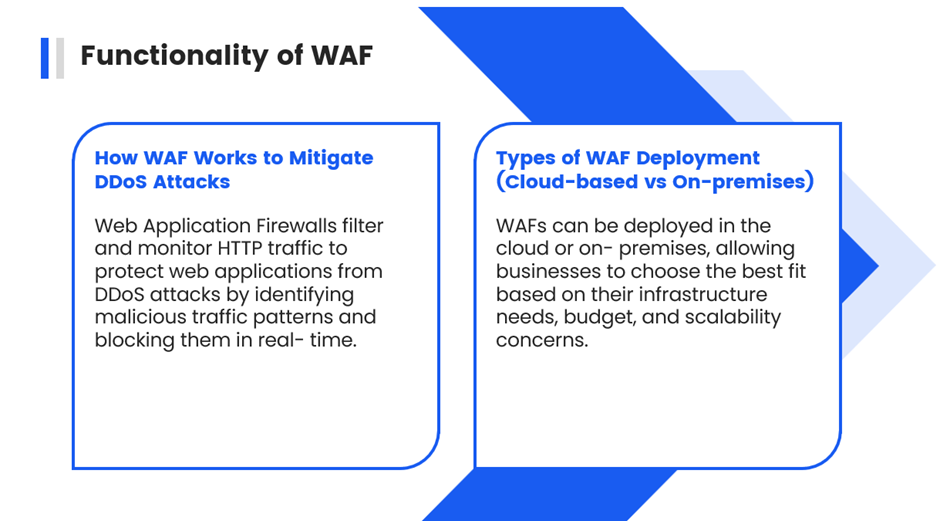
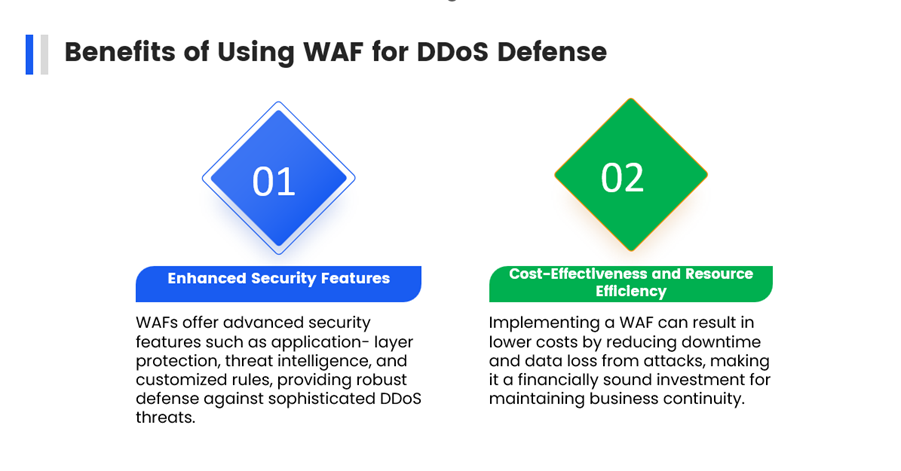
iii. Use Web Application Firewalls (WAF)
A WAF can filter and monitor HTTP traffic between a web application and the internet, protecting against application-layer attacks.
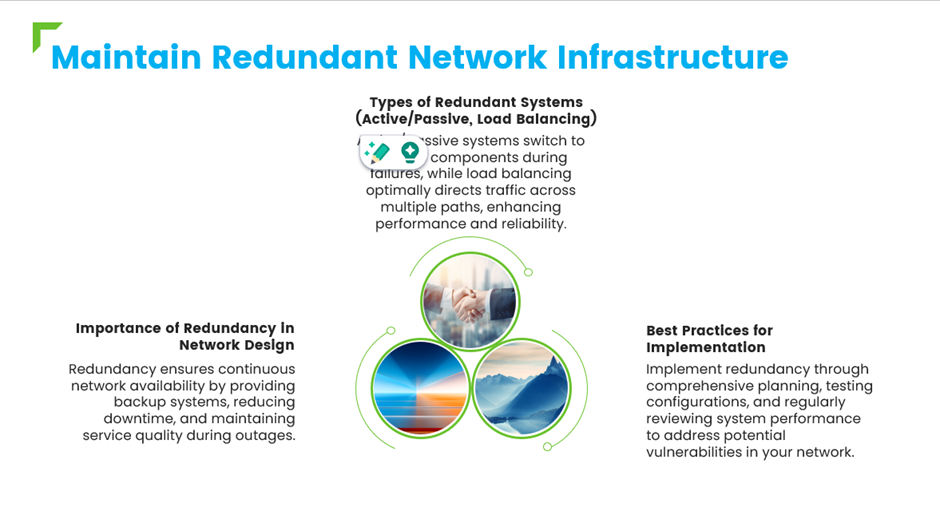
iv. Maintain Redundant Network Infrastructure
Having multiple data centers and network paths can help distribute traffic and maintain service availability during an attack.
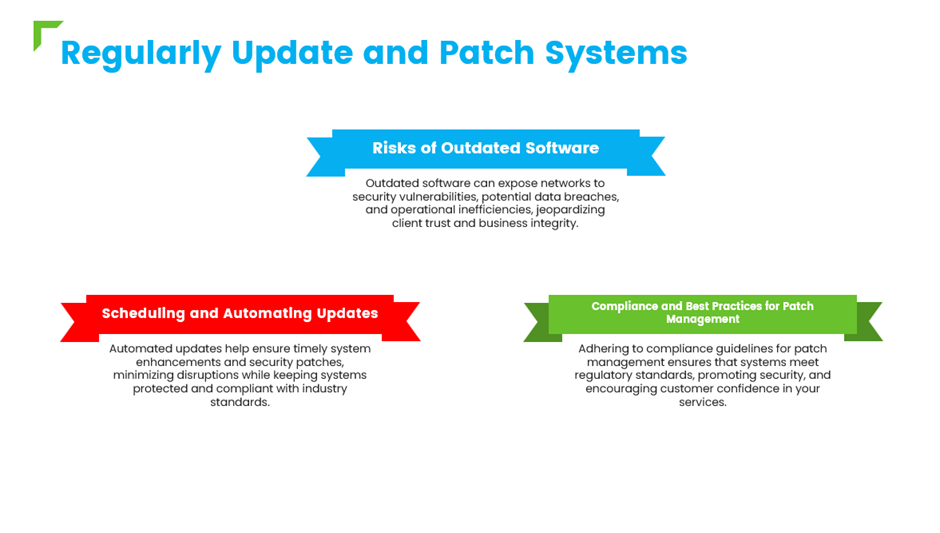
v. Regularly Update and Patch Systems
Ensure all systems and applications are up-to-date with the latest security patches to prevent exploitation of known vulnerabilities.

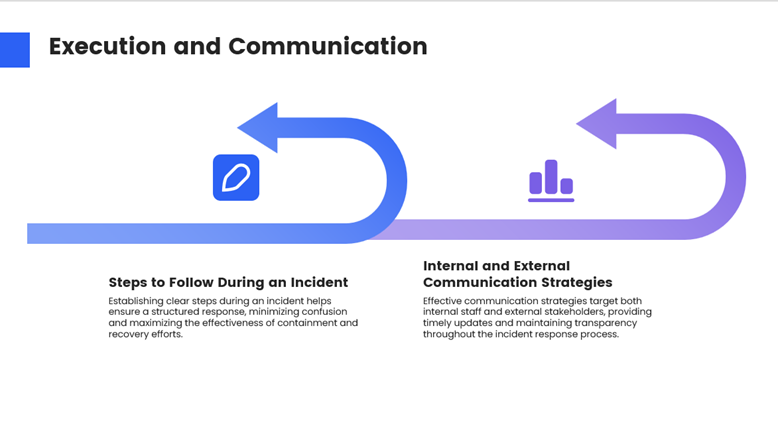
vi. Develop an Incident Response Plan
Prepare a comprehensive response plan outlining steps to take during a DDoS attack, including communication strategies and recovery procedures.
Conclusion
DDoS attacks pose a significant threat to organisations, with the potential to cause substantial financial and reputational damage. As attackers continue to develop more sophisticated methods, organisations must stay ahead by implementing robust security measures and staying informed about the latest trends in cybersecurity.
By understanding the nature of DDoS attacks and adopting a proactive approach to defence, organisations can safeguard their digital assets and ensure the continuity of their services.






