IAM Misconceptions That Could Cost You
Many businesses still rely on top myths about Identity and Access Management; even if these “cybermyths” might have made sense years ago, your organisation is at risk in today’s world of cloud apps, remote teams, and AI-driven threats. In this blog, we’ll debunk the most common IAM misconceptions holding companies back. You’ll discover what’s changed, why legacy thinking no longer works, and how to build a smarter, modern IAM strategy that protects your digital assets.

Source- https://www.weforum.org/stories/2025/02/biggest-cybersecurity-threats-2025/
Let’s clear up the confusion and set the record straight.
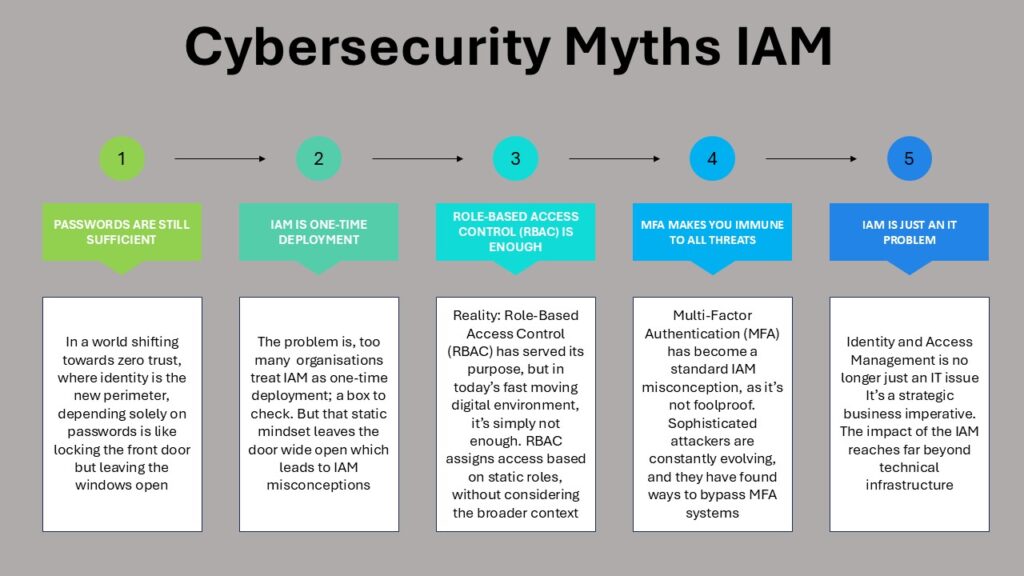
Cybersecurity myths IAM 1: Passwords Are Still Sufficient
Reality: Let’s face it; passwords have had their run, but they’re no longer up to the job.
Even with multi-factor authentication (MFA) in play, attackers are getting smarter, using phishing tactics and social engineering to sneak past the gates. It’s time we move beyond outdated common cybersecurity misconceptions in IAM systems and lean into what works: phishing-resistant authentication. Technologies like FIDO2 and biometrics are game-changers. FIDO2 relies on cryptographic keys that stay locked to your device, rendering common phishing methods useless. Biometric authentication, like a fingerprint or facial recognition, adds a personal, unforgeable layer of security. In a world shifting towards zero trust, where identity is the new perimeter, depending solely on passwords is like locking the front door but leaving the windows open. By adopting modern, passwordless solutions, organizations not only close the loopholes but also give users a smoother, more intuitive experience by decluttering Zero Trust IAM myths. The future of secure access isn’t just passwordless; it’s smarter, faster, and built around trust that can’t be faked.
Cybersecurity myths IAM 2: IAM Is a One-Time Deployment
Reality: Identity and Access Management (IAM) isn’t just a security tool; it’s a living, evolving practice that needs to adapt as your business and risks grow. At its core, IAM is a continuous lifecycle. It starts with governing who has access to what, reviewing that access regularly, and adjusting based on real-time risk signals. That means constantly asking: Does this user still need this level of access? Has their role changed? Are there any unusual behaviors that might indicate misuse?
The problem is, too many organizations treat IAM as a one-time deployment, a box to check. But that static mindset leaves the door wide open, which leads to IAM misconceptions. Threats evolve fast, and insider risks are often overlooked until it’s too late. Whether it’s an employee misusing credentials or an external actor slipping through weak points, the damage can be significant.
To truly protect against modern threats, IAM systems must be dynamic. They need to learn, respond, and adapt in real time. That includes automated access reviews, intelligent alerts, and seamless integration with other security layers. It’s not just about blocking threats; it’s about enabling the right access, at the right time, for the right reasons. That’s the future of IAM, and it’s already here.
Cybersecurity myths IAM 3: Role-Based Access Control (RBAC) Is Enough
Reality: Role-Based Access Control (RBAC) has served its purpose, but in today’s fast-moving digital environment, it’s simply not enough. RBAC assigns access based on static roles, without considering the broader context of how, when, or where that access is used. That’s a serious limitation. Modern identity systems demand more than just role-matching; they require intelligent, context-aware decision-making. This is where Attribute-Based Access Control (ABAC) comes in. ABAC evaluates attributes like user identity, device health, location, time of access, and even behavioral patterns to make real-time access decisions. It’s a smarter, more flexible approach that aligns perfectly with zero trust principles.
By shifting to policy-driven access control, organizations can dynamically adapt to changing risk scenarios. For example, a user logging in from a trusted device during business hours might be granted access, while the same request from an unknown location at midnight could be flagged or denied. That level of granularity simply isn’t possible with traditional RBAC models.
To keep pace with evolving threats and complex work environments, businesses need access control that reflects real-world context. ABAC isn’t just the future; it’s the now. Embracing it means stronger security, better compliance, and smarter user experiences.
Cybersecurity myths IAM 4: MFA Makes You Immune to All Threats
Reality: Multi-Factor Authentication (MFA) has become a standard IAM misconception, as it’s not foolproof. Sophisticated attackers are constantly evolving, and they’ve found ways to bypass even well-implemented MFA systems. Tactics like SIM-swapping, man-in-the-middle (MITM) attacks, and the theft of session tokens can easily undermine traditional MFA. These aren’t theoretical risks; they’re happening in real-world breaches across industries. That’s why relying on static authentication checkpoints isn’t enough anymore.
The real defense lies in continuous and adaptive authentication solutions that monitor user behavior, device integrity, and contextual signals in real time. Instead of verifying identity just once at login, adaptive authentication keeps checking in silently throughout the session. Is the user’s behavior consistent with their profile? Has the device suddenly changed? Is access coming from a suspicious location? These signals allow systems to respond instantly, tightening access when something feels off.
For organizations serious about cybersecurity, moving beyond basic MFA is no longer optional. Continuous authentication provides the resilience needed to stay ahead of modern threats while improving the user experience with frictionless security. It’s a smarter, more responsive layer of protection, built for today’s complex threat landscape
Cybersecurity myths IAM 5: IAM Is Just an IT Problem
Reality: Identity and Access Management (IAM) is no longer just an IT issue; it’s a strategic business imperative. The impact of IAM reaches far beyond technical infrastructure. It directly influences business continuity, regulatory compliance, insider threat detection, and even the overall customer experience. When done right, IAM ensures that the right people have the right access at the right time, without delays or risk exposure. That seamless control is what keeps operations running smoothly during everything from routine audits to crises.
For compliance, IAM plays a central role in enforcing policies, maintaining audit trails, and reducing the risk of violations that can lead to heavy penalties. It also provides early indicators of insider threats through behavioral monitoring and intelligent access reviews, critical in today’s high-risk environments. On the customer side, frictionless, secure login experiences powered by modern IAM frameworks translate to higher trust and satisfaction.
This is why IAM belongs in C-suite conversations and boardroom agendas. It’s not just about managing user accounts; it’s about enabling secure growth, building digital trust, and protecting the business at every level. Companies that prioritise IAM as a business enabler, not a backend task, are the ones better equipped to compete in today’s threat-heavy, compliance-driven landscape.
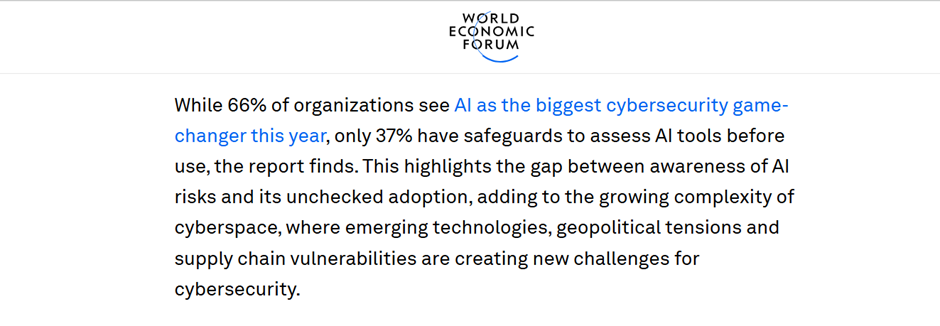
Source- https://www.weforum.org/stories/2025/02/biggest-cybersecurity-threats-2025/
Preparing IAM for the Quantum Threat
Quantum computing threatens to break widely used public-key cryptography (RSA, ECC), exposing cybersecurity myths in IAM systems to future breaches. The current scenario in the cybersecurity organisation, facing a decline in cybersecurity leaders to resist real-time threats, making the landscape a quantum computing-friendly.
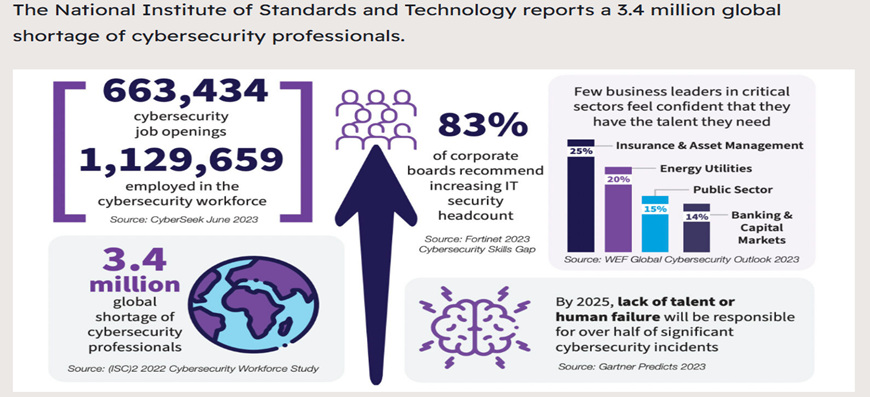
Source- https://identitytheft.org/statistics/cyber-security/
How Organisations Are Responding
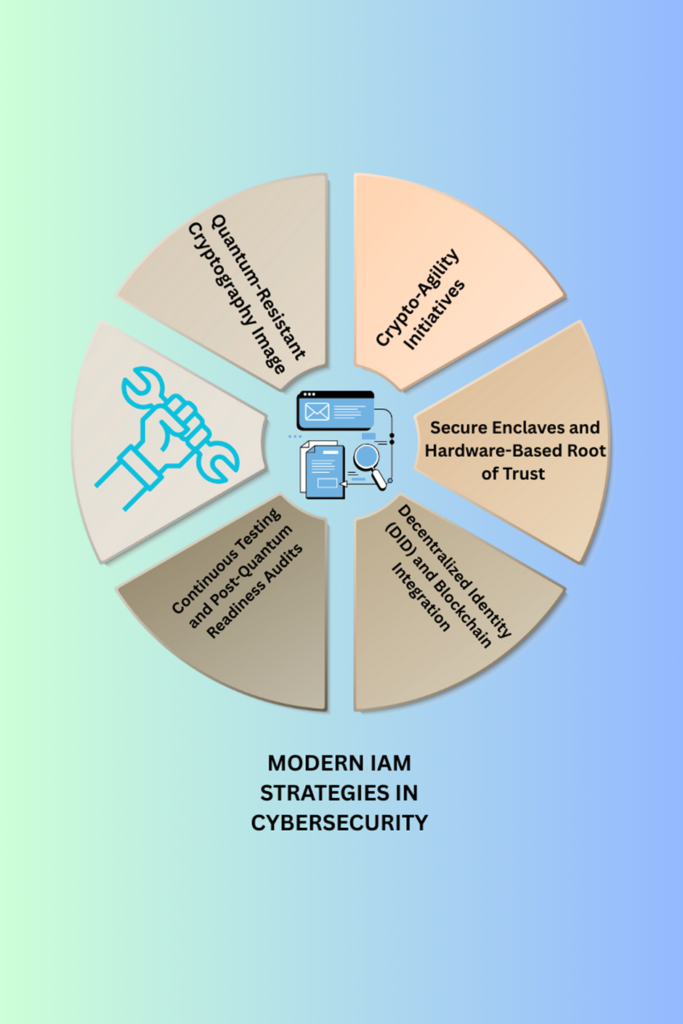
Quantum-Resistant Cryptography
Forward-thinking IAM vendors and enterprises are already preparing for the quantum era by testing post-quantum cryptographic algorithms like lattice-based and hash-based encryption. These cutting-edge approaches are being explored to future-proof Public Key Infrastructure (PKI), TLS protocols, and digital certificates. As quantum computing threatens to break current encryption standards, adopting quantum-resistant algorithms is becoming a cybersecurity priority. The shift isn’t just technical; it’s a proactive move to secure trust, data integrity, and long-term digital resilience
Crypto-Agility Initiatives
Modern IAM systems are being built with crypto-agility at their core, meaning they can adapt quickly as cryptographic standards evolve. Instead of requiring a full infrastructure overhaul, these systems allow seamless swapping of cryptographic primitives like algorithms and keys. This flexibility is essential in a world facing quantum threats and rapid cryptographic advancements. Crypto-agile IAM ensures long-term resilience, compliance readiness, and smoother transitions as organizations adopt post-quantum and hybrid encryption models. It’s proactive, smart security built for what’s next.
Secure Enclaves and Hardware-Based Root of Trust
To stay ahead of quantum threats, forward-looking IAM strategies now leverage Trusted Platform Modules (TPMs), Hardware Security Modules (HSMs), and confidential computing environments. These technologies strengthen credential storage and secure cryptographic operations by isolating sensitive processes from exposure. TPMs and HSMs provide hardware-level protection, while confidential computing ensures data remains encrypted even during processing. Together, they build a robust, quantum-resilient foundation for identity systems, boosting trust, integrity, and future-proof security
Decentralized Identity (DID) and Blockchain Integration
Self-sovereign identities (SSIs) and verifiable credentials are reshaping digital trust by giving users full control over their identity data. Built on quantum-resistant blockchains, these decentralized systems offer tamper-proof, privacy-preserving authentication without relying on central authorities. Early pilots show how SSIs can streamline access, enhance user privacy, and withstand future quantum threats. It’s a bold shift toward user-controlled, resilient identity ecosystems, aligning security, autonomy, and innovation.
Continuous Testing and Post-Quantum Readiness Audits
Forward-looking organizations are actively aligning with NIST’s Post-Quantum Cryptography (PQC) standardization efforts to future-proof their IAM infrastructure. They’re conducting quantum risk impact assessments across identity pipelines to uncover potential vulnerabilities and plan for secure transitions. This proactive approach ensures cryptographic agility, long-term compliance, and resilience against quantum-era threats. By integrating PQC strategies now, enterprises are building identity systems that are not only secure today but designed to withstand the security challenges of tomorrow
Organisations that treat IAM as static are falling behind. The real leaders are:

Navigating the way for a modern IAM system in cybersecurity(conclusion)
Future-proofing their identity stack against the quantum computing era. IAM is no longer about who has access; it’s about dynamic, secure trust in a world where algorithms, attackers, and quantum capabilities evolve every day.
Source – https://cybelangel.com/quantum-safe-cybersecurity/
Source – https://support.apple.com/en-in/guide/security/sec59b0b31ff/web