The shift no one is talking about loudly enough
Identity and Access Management (IAM) has always relied on rules. Define a role. Assign permissions. Create approval workflows. Review periodically. Repeat.
For years, this rule-based model worked because environments were predictable.
Today, they are not.
Enterprises are now managing:
- hybrid workforces
- millions of machine identities
- multi-cloud applications
- constantly changing vendor ecosystems
- evolving compliance frameworks
The traditional IAM model was built for stability. The world now operates on volatility.
This is where Autonomous IAM enters the conversation; not as a trend, but as a structural necessity.
Why rule-based IAM is reaching its limit
Rule-based IAM assumes:
- access patterns remain stable
- roles reflect real behaviour
- periodic reviews are sufficient
- risks are predictable
Global incidents over the past few years have exposed the fragility of these assumptions.
Across industries, breaches have frequently occurred because:
- excessive access was never reviewed
- permissions accumulated over time
- dormant accounts remained active
- anomaly signals were ignored due to volume
In many cases, attackers did not exploit vulnerabilities; they exploited existing, legitimate access.
The pain is not technological.
It is architectural.
The global identity challenge we’re facing
Real-time enterprise realities show a clear pattern:
- Employees change roles faster than access models update
- Cloud adoption outpaces governance structures
- Machine identities now outnumber human users
- Manual access reviews create fatigue, not clarity
- Compliance audits demand explainability
The most surprising element?
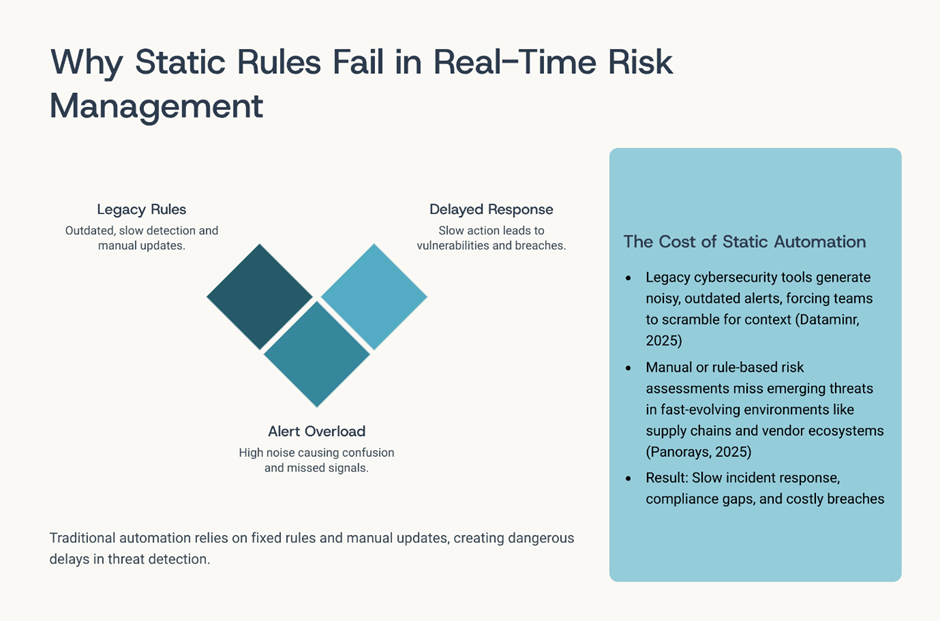
Many organisations believe they are “automated” because workflows are digitised. But automation without intelligence is still rule-bound.
When risk changes in real time, static rules become blind.
What autonomous IAM actually means

Autonomous IAM is not about removing humans from identity governance.
It is about shifting from static rule enforcement to adaptive decision-making.
In practical terms, it means systems that:
- learn normal access patterns
- detect behavioural deviations automatically
- adjust permissions based on usage
- prioritise high-risk identities
- continuously validate trust
Instead of asking:
“Does this request match a rule?”
Autonomous IAM asks:
“Does this behaviour match intent and context?”
That shift changes everything.
The pain points leaders are quietly confronting
In boardrooms and executive reviews, identity rarely dominates headlines until something goes wrong. Yet beneath the surface of digital transformation initiatives, identity-related friction continues to grow. Leaders sense it in delayed projects, audit observations, unexplained access escalations, and rising operational fatigue. The challenge is not a lack of IAM tools. It is the growing gap between static governance models and dynamic enterprise realities.
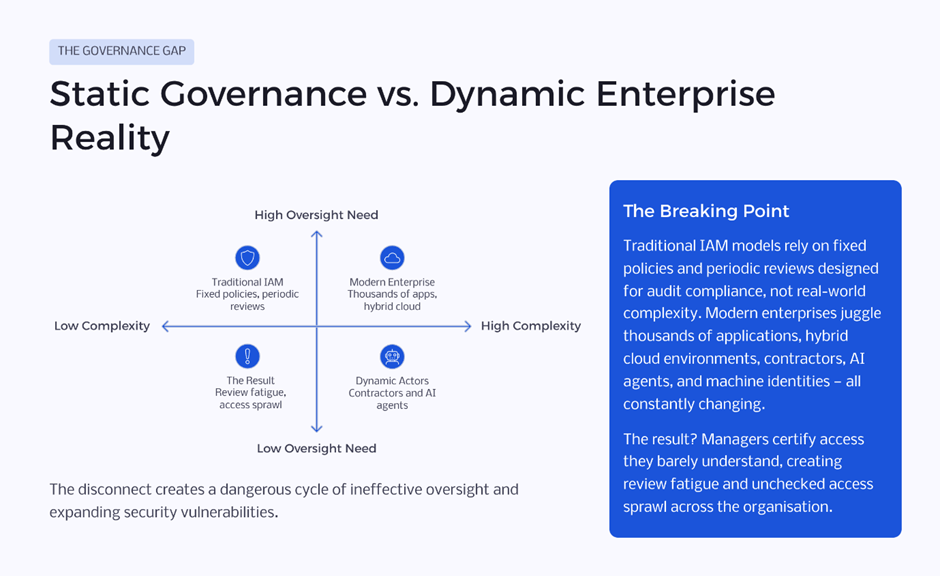
As organisations expand across cloud platforms, vendor ecosystems, and distributed teams, identity complexity compounds quietly. Each new system, integration, and access exception adds another layer of invisible risk. The danger is subtle: nothing appears broken until accumulated access becomes a liability.
The concerns leaders are navigating today are not theoretical. They are operational, financial, and reputational.
1. Access Sprawl
Over time, permissions accumulate faster than they are removed. Promotions, project shifts, temporary assignments, and vendor engagements leave behind residual access.
- Users retain privileges they no longer need.
- Role definitions become outdated.
- Least-privilege principles erode gradually.
- Identity debt grows invisibly.
This sprawl expands attack surfaces and complicates accountability.
2. Audit Fatigue
Access certifications are meant to reduce risk, but when conducted manually at scale, they become repetitive and shallow.
- Reviewers approve in bulk due to time pressure.
- Risk prioritisation is weak or absent.
- Evidence collection becomes labour-intensive.
- Compliance feels procedural rather than protective.
The result is governance that satisfies requirements without truly reducing exposure.
3. Machine Identity Explosion
Service accounts, APIs, bots, cloud workloads, and IoT devices now outnumber human users in many enterprises.
- Machine credentials often lack clear ownership.
- Rotation policies are inconsistently enforced.
- Access remains static despite changing behaviour.
- Visibility across systems is fragmented.
Traditional IAM models were never designed for this scale of non-human identity growth.
4. Reactive Incident Response
When misuse occurs, investigations frequently reveal that access was legitimate but misaligned.
- Dormant accounts are rediscovered after compromise.
- Privileged permissions were technically valid.
- Anomalies were buried in alert volume.
- Response time is slowed by unclear ownership.
Identity governance becomes investigative rather than preventative.
5. Decision Overload
Security and IT teams are overwhelmed by approvals, exception handling, and alert triage.
- Approval chains grow longer.
- Risk signals compete for attention.
- Manual judgment is stretched thin.
- Strategic thinking is replaced by operational firefighting.
The cumulative impact is leadership fatigue, where control feels present, but clarity feels absent.
These pain points are interconnected; access sprawl fuels audit fatigue. Machine identities amplify visibility gaps. Reactive response drains strategic capacity. The core issue is not capability; it is adaptability.
Rule-based IAM struggles because it assumes stability in a world defined by change. Until identity systems become context-aware and self-adjusting, these quiet pressures will continue to intensify. Recognising these pain points early is not a sign of weakness. It is the first step toward designing identity governance that scales with reality rather than resisting it.
How self-learning IAM systems change the equation
Autonomous IAM introduces intelligence into identity governance.
Here’s how it reshapes the landscape:
Continuous Behaviour Analysis
- Learns typical access behaviour
- Flags anomalies in real time
- Reduces false positives
Context-Aware Access Decisions
- Evaluates time, device, location, and role changes
- Adjusts trust dynamically
Automated Access Optimisation
- Identifies unused permissions
- Recommends removal
- Reduces identity debt
Risk-Based Prioritisation
- Focuses reviews on high-impact accounts
- Minimises low-risk noise
Adaptive Policy Evolution
- Policies improve as the system learns
- Reduces dependency on static role definitions

This is not a futuristic theory. Enterprises globally are already integrating AI-driven IAM models to manage scale.
Why this is becoming a CXO-level priority
Autonomous IAM intersects with:
- Cybersecurity resilience
- Regulatory compliance
- Cloud cost optimisation
- Operational efficiency
- Digital trust
When identity decisions are intelligent and adaptive, leaders gain:
- clearer visibility into risk
- faster response times
- fewer unnecessary approvals
- reduced operational burden
Autonomous IAM transforms identity from an operational bottleneck into a strategic control layer.
The risks of moving too fast
While the promise is strong, leadership must proceed deliberately.
Autonomous IAM fails when:
- governance is unclear
- ownership of identity decisions is undefined
- AI operates without explainability
- automation amplifies flawed policies

Intelligence without governance can scale risk faster than rules ever did.
The goal is adaptive systems with accountable oversight.
Practical steps toward autonomous IAM
For CXOs considering this transition, the shift does not require immediate overhaul.
It begins with:
1. Cleaning Identity Foundations
- Remove orphaned accounts
- Reduce unnecessary access
- Clarify ownership
2. Introducing Behavioural Monitoring
- Layer intelligence over existing IAM
- Start with high-risk systems
3. Prioritising High-Impact Identities
- Focus on privileged accounts
- Monitor machine identities
4. Defining Governance Boundaries
- Determine where human oversight remains mandatory
- Establish explainability standards
5. Measuring Intelligence Outcomes
- Reduction in access sprawl
- Faster anomaly detection
- Improved audit clarity
Autonomy should be incremental, not abrupt.
What the future looks like
Over the next five years, Identity and Access Management will undergo one of the most significant transformations since its inception. What was once a structured, rule-based control layer will become a dynamic, intelligence-driven system capable of adapting in real time. As enterprises expand across hybrid cloud environments, remote workforces, APIs, and machine ecosystems, IAM will no longer operate as a static gatekeeper. It will function as a continuously learning trust engine.

The evolution will not be dramatic in appearance, but foundational in impact. Identity systems will gradually move from enforcing predefined rules to interpreting behaviour, context, and risk signals as they emerge. Instead of waiting for periodic reviews or manual triggers, systems will continuously assess whether access still aligns with purpose and intent. This shift will redefine how organisations think about digital trust.
Over the next five years, IAM will evolve toward:
- Continuous trust validation
Access will no longer be granted and forgotten. Systems will constantly reassess whether an identity, human or machine, still deserves its level of access based on behaviour, environment, and risk signals. - Predictive access adjustments
Rather than reacting to misuse, IAM platforms will anticipate over-provisioning, recommend privilege reductions, and proactively flag unusual access trajectories before incidents occur. - Reduced manual approval chains
Routine, low-risk access decisions will be automated intelligently, freeing leaders and security teams to focus only on high-impact scenarios that require judgment. - Intelligent identity lifecycle management
Access will automatically adjust as roles change, projects conclude, or vendor relationships end, preventing the accumulation of identity debt. - Seamless integration with Zero Trust security models
IAM will serve as the real-time decision engine behind Zero Trust, continuously validating identity rather than relying on network boundaries.
As these capabilities mature, the distinction between identity management and security monitoring will begin to blur. Identity will no longer be a supporting function; it will become the control layer through which risk is evaluated continuously.
Identity systems will not just enforce rules.
They will understand context, interpret behaviour, and adapt trust dynamically, making IAM not only smarter, but fundamentally more aligned with how modern enterprises operate.
A Surprising Reality
The greatest risk facing identity governance today is not cyber-attack sophistication; it is inertia. Organisations that remain committed to static rule-based IAM models will struggle to keep pace with digital transformation. The scale of modern enterprise ecosystems demands adaptability.

Autonomous IAM is not about replacing people.
It is about enabling them to focus on judgment rather than repetition.
Towards an optimistic path
Autonomous IAM represents the next stage of digital identity transformation.
It is not a silver bullet.
It is not a plug-and-play solution.
It is an evolution from rigid rule enforcement to intelligent, adaptive governance.
The organisations that succeed will not be those who automate everything blindly. They will be those who combine:
- strong governance
- accountable leadership
- explainable AI
- disciplined implementation
In a world where trust must be earned continuously, identity systems must learn continuously.
The transition from rule-based to self-learning IAM is not about complexity.
It is about relevance.
And the leaders who recognise this early will not just secure their organisations; they will future-proof them.






