09 April 2025 – 10 mins. Read
By: Gagan K. Mathur – IAM Strategist | Cybersecurity Leader | Future-Ready Visionary
Introduction: The Rising Tide of Identity-Based Threats
In the world today, with its hyper-connectivity, identity is both the new perimeter and the most compromised attack vector. Threat actors don’t break in anymore—they log in. Credentials are readily available on the dark web, and advanced phishing kits are plentiful, so identity-based attacks are booming.

Static Access Policies and Rule-Based Systems won’t keep up with the pace or sophistication of today’s identity threats. That’s where AI-Driven Threat Detection enters the picture – with the capability to detect, prevent, and thwart identity-based threats in real-time.
What is AI-Driven Threat Detection in IAM?
AI-Driven Threat Detection uses Artificial Intelligence (AI), Machine Learning (ML), Behavior Analytics, and Context Awareness to continuously monitor identity events. Unlike rules-based solutions, AI models learn from historical behavior, identify subtle anomalies, and react dynamically.
It’s proactive, not reactive. It’s like, instead of waiting for someone to steal your stuff, it figures out they’re about to and stops them.
The Tech That Makes It Work
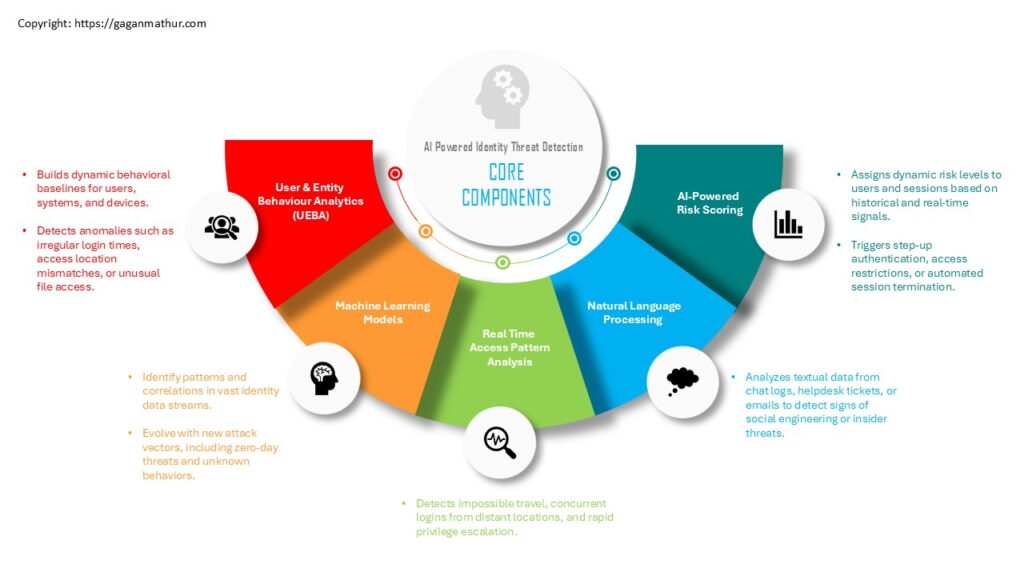
1.) User & Entity Behavior Analytics (UEBA)
- Creates comprehensive behavior baselines through the observation of normal patterns of users, systems, and devices throughout the enterprise.
- Identifies anomalies from these baselines, like abnormal work hours, abnormal device usage, excessive data download, or off-normal geographic access, which might represent compromised accounts or insider attacks.
- Uses peer group analysis to identify outliers across similar jobs or departments.
2.) Machine Learning Models
- Use supervised and unsupervised learning models to continually update detection capabilities according to changing threat patterns.
- Detect long-term changes in user behavior, correlating seemingly harmless events to reveal sophisticated attack chains.
- Identify zero-day attacks and emerging threat vectors without the need for pre-defined signatures.
3.) Real-Time Access Pattern Analysis
- Constantly monitors access events for anomalies such as impossible travel (e.g., logins from two geographies minutes apart), simultaneous sessions from disparate geographies, or fast lateral movements between systems.
- Correlates behavioral anomalies against recognized tactics, techniques, and procedures (TTPs) through models such as MITRE ATT&CK
4.) Natural Language Processing (NLP)
- Normalizes unstructured data from emails, support tickets, chat platforms, and logs to find indicators of phishing, social engineering, or policy abuse.
- Recognizes changes in tone or language red flags indicating potential coercion or malicious insider behavior.
- Is able to flag potentially sensitive combination words, suspect requests, or escalations requests relating to privileges
5.) AI-Based Risk Scoring
- Assesses a real-time, dynamic risk rating for every session or user taking into consideration countless signals across the spectrum—from device reputation through to login environment, past behaviors, and anomaly-related behaviors.
- Supports smart decision-making by IAM systems, i.e., triggering adaptive authentication (MFA), limiting access, or starting automated incident response playbooks.
- Empowers human analysts’ prioritization by flagging sessions or users that need priority examination.
Why Traditional IAM Needs AI
Even though traditional IAM systems are critical, they were not designed to manage the volume, complexity, and dynamics of today’s identity threats. They are overly dependent on static policies, pre-programmed rules, and review-by-schedule – none of which are effective against today’s dynamic threat landscape.
🔄Volume & Velocity Outpace Manual Systems
Today’s businesses produce millions of identity-related events per day – from logins and privilege escalations to access requests and third-party interactions. Static rules just can’t handle this quantity efficiently, and human analysts simply can’t cope with the flood of alerts. AI does the heavy lifting by detecting risky patterns at machine speed.
🕵️♂️Sophisticated Threats Mimic Legitimate Behavior
Attackers today don’t merely brute-force their way in – they discover user behavior, mimic access patterns, and blend in with regular traffic. Legacy IAM systems can’t distinguish between an actual user and a clever impersonator. AI, aided by behavioral analytics and anomaly detection, can notify even slight deviation rule-based systems miss.
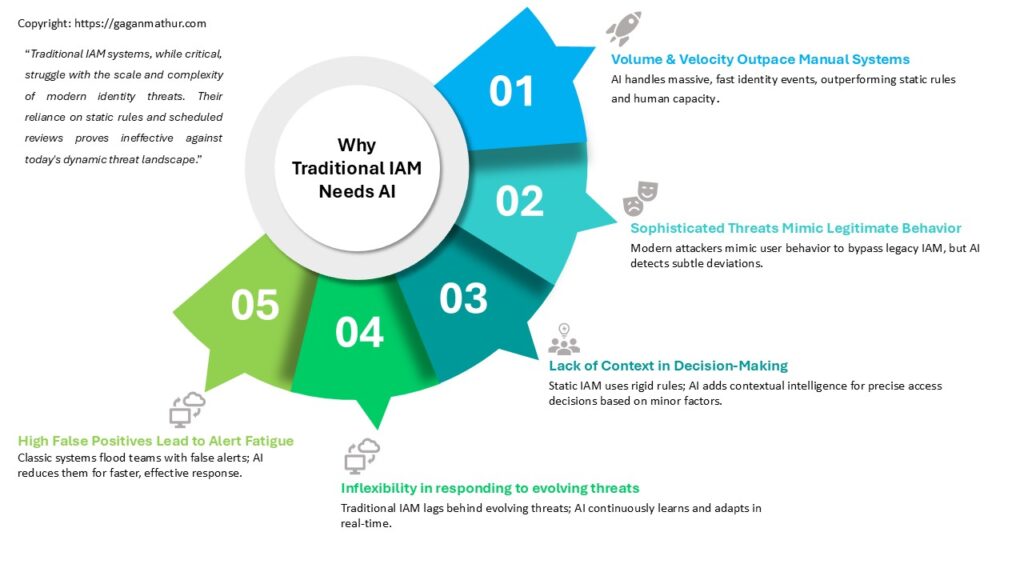
🧠Lack of Context in Decision-Making
Static IAM products generally operate with binary logic – permit or deny – on predetermined policies and roles. They fail to consider minor factors like time of login, device reputation, history of action, or group peer activity. AI brings in contextual intelligence, enabling more accurate, context-relevant access control decisions.
🔁Inflexibility in Responding to Evolving Threats
Threat actors never cease to innovate. But traditional IAM policies fall behind, requiring manual adjustment and revision. AI models, however, learn continuously from new data. They adjust in real-time, detecting new tactics in flight without requiring human intervention or policy revisions.
🚨High False Positives Lead to Alert Fatigue
The classic systems have a tendency to bombarding security teams with false alerts, hiding real threats in the noise. AI reduces the false positives by refining risk scoring models and constantly improving. The result? Reduced fatigue, faster triage, and more effective incident response.
Use Cases Across Industries
AI-Powered Identity Threat Detection isn’t one-size-fits-all solution. It’s evolving according to sector-based threats, and that’s where the solution lies to make it affordable for any business in any field to take their identity protection to the next level. This is how different markets are leveraging its capabilities:
🏦Banking & Financial Services
AI plays a pivotal role in one of the most targeted industries –
- Flagging Suspicious Transactions: Identifying unusual money transfers, rapid transaction bursts, or login attempts from high-risk geolocations.
- Watching for Privilege Escalation: Notifying on unauthorized role changes, particularly within high-value systems such as trading systems or SWIFT networks.
- Preventing Account Takeovers: Real-time alerts for bot-initiated credential stuffing or phishing attacks – particularly customer login spikes (e.g., month-ends, tax due).
🏥Healthcare
With sensitive patient information at risk, AI protects healthcare systems by:
- Protecting Electronic Health Records (EHRs): Detection of unauthorized patient data access by internal personnel or third-party suppliers, particularly during non-working hours or patient treatment history.
- Securing Medical Devices: Tracking device-system interaction and reporting` device function abnormalities or data access attempts.
- Insider Threat Prevention: Abuse pattern detection, i.e., employees snooping into friends, celebrities, or prominent patients records.
🛍️Retail & E-Commerce
Transaction volume and customer trust make the retail sector a target of choice for identity misuse. AI assists by:
- Preventing Credential Stuffing Attacks: Anomaly detection of low-success, suspicious logins and blocking botnets attempting stolen credentials from the dark web.
- Identification of Seasonal Traffic Peaks: Differentiation between genuine customer traffic and attacker spikes caused by events such as Black Friday or product releases.
- Prevention of Gift Card & Loyalty Abuse: Detection of suspicious access to customer reward programs or bulk redemptions of promotional credits.
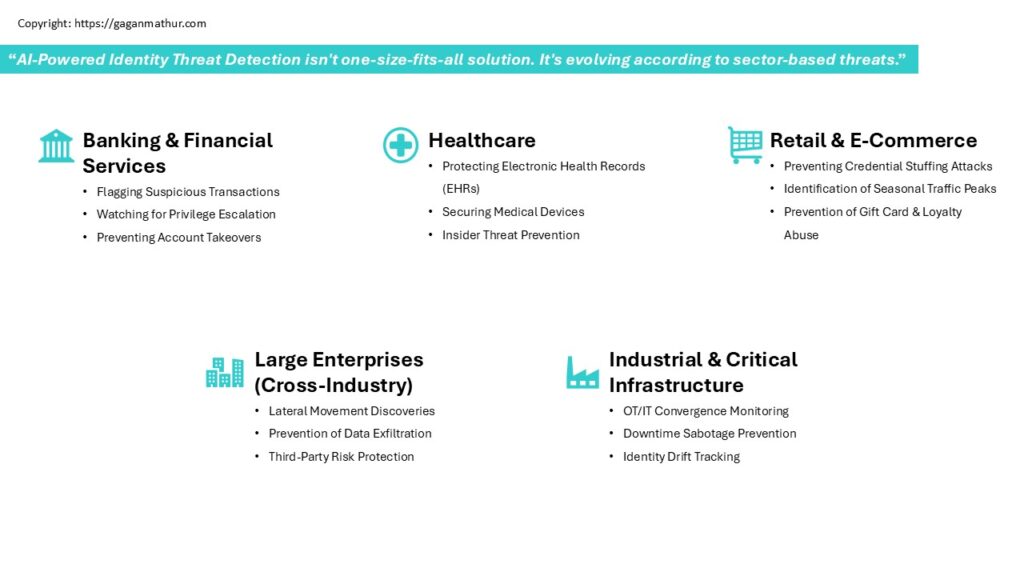
🏢Large Enterprises (Cross-Industry)
Across multinational organizations, AI assists in:
- Lateral Movement Discoveries: Detection when a compromised identity is roaming department to department, system to system, or geography to geography.
- Prevention of Data Exfiltration: Detection of suspicious data access patterns, including bulk downloads in anticipation of resignation or off-cloud exports to cloud drives.
- Third-Party Risk Protection: Monitoring contractor, vendor, and remote user activity whose access credentials are different from internal employees.
⚙️Industrial & Critical Infrastructure
In energy, manufacturing, and utility industries, AI protects operation integrity by:
- OT/IT Convergence Monitoring: Identifying illicit access between interlinked IT systems and operational technology.
- Downtime Sabotage Prevention: Triggering anomalies that may indicate an impending system shut-down or industrial control system compromise.
- Identity Drift Tracking: Keeping pace with identity roles and permissions accumulating against operational needs, particularly for users of legacy systems.
AI-driven detection is not just about identifying threats – it’s about tailoring defense to the unique identity landscape of each industry. Context-aware security creates tighter defense, quicker response times, and sustainable trust.
Tangible Benefits
Incorporating AI into Identity Threat Detection is not just a technical boost – it’s a business driver. From improved security posture to optimized operations, the advantages span functions and departments. Here’s a closer look at the quantifiable effects organizations can expect:
✅ Early Detection & Real-Time Response
AI solutions are continuously monitoring for access patterns and identity behavior—enabling anomalies to be caught in seconds, rather than days. Whether it is the alert of a compromised admin account or malicious service accessing privileged information, AI allows organizations to:
- Prevent the attack chain before the initiation of lateral movement.
- Automate triggering mitigation actions like access revocation, enforced MFA, or session termination.
- Gain crucial time during zero-day or insider threat scenarios.
✅ Minimize False Positives
Legacy systems are notorious for alert fatigue, flooding analysts with thousands of false alerts. AI improves signal-to-noise ratio by:
- Learning and adapting to user-specific baselines.
- Correlating seemingly unrelated events into a coherent risk narrative.
- Reducing triage time and enabling SOC teams to focus on truly suspicious activity.
Outcome: Better team productivity and faster Mean Time to Detect (MTTD).
✅ Frictionless User Experience
Security should never come at the cost of usability. AI ensures:
- Context-aware authentication: Step-up verification is requested only when behavior is suspicious or risk score surges.
- Least disruptions: Authenticated users can use systems without much friction, leading to increased productivity and satisfaction.
- Adaptive controls: AI adjusts access policies dynamically as a function of the dynamic trust level of each session or identity.
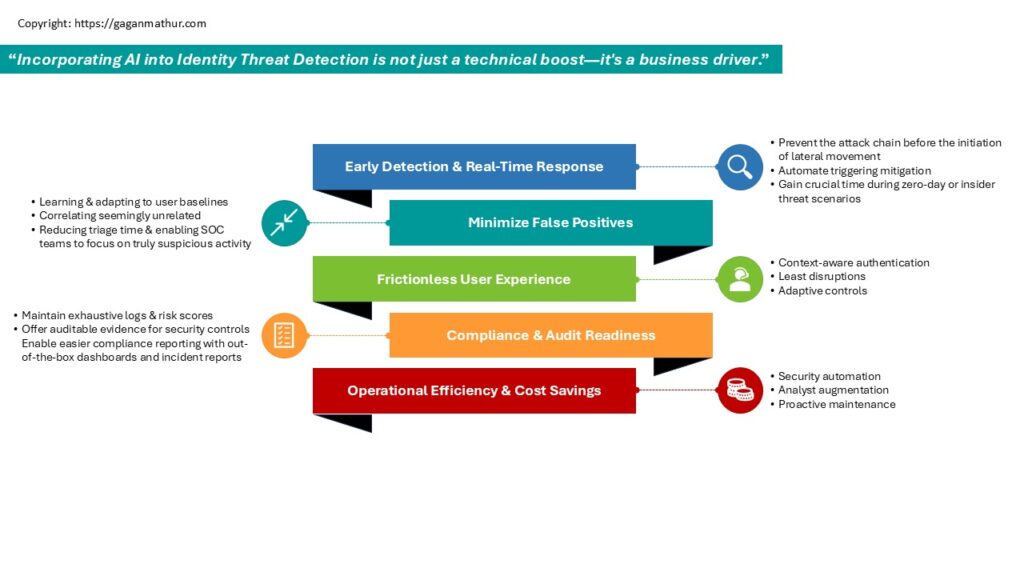
✅ Compliance & Audit Readiness
Regulations like GDPR, HIPAA, SOX, and NIST mandate constant monitoring and reporting. AI systems:
- Maintain exhaustive logs and risk scores for every identity event.
- Offer auditable evidence for security controls and decisions.
- Enable easier compliance reporting with out-of-the-box dashboards and incident reports.
Bonus: Some AI products include explainability capabilities to assist with detection results in audits.
✅ Operational Efficiency & Cost Savings
AI augments human teams, rather than replacing them. It enables:
- Security automation: AI interworks with SOAR and EDR tools to auto-triage and respond to low-risk incidents.
- Analyst augmentation: Allowing junior analysts to be threat-aware faster with contextual guidance and root cause analysis.
- Proactive maintenance: Allow identification of stale or inactive accounts and suspicious access patterns, allowing IAM teams to be able to mitigate access sprawl.
Long-term impact: Lowered breach costs, reduced headcount pressure, and smarter identity governance.
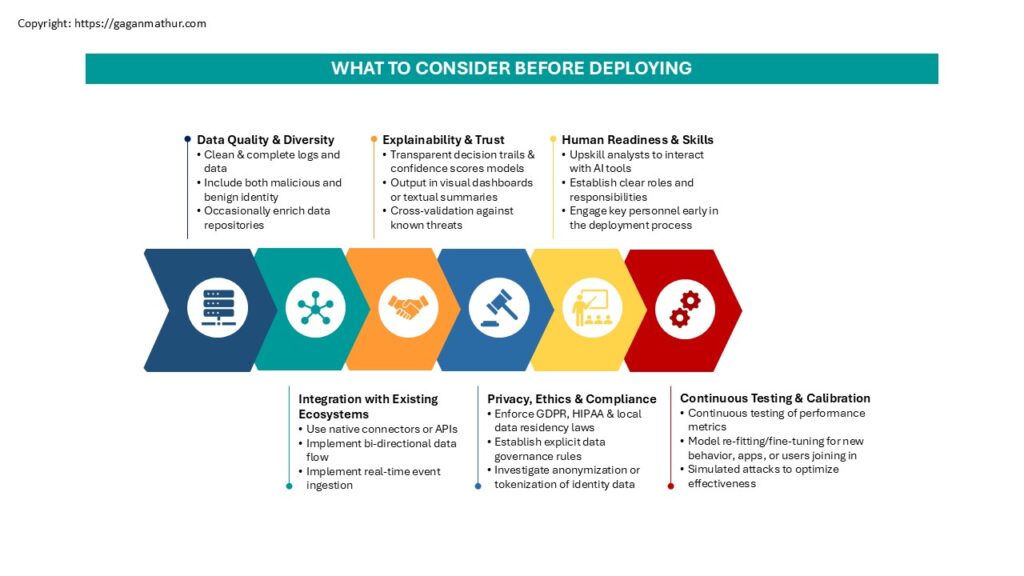
What to Consider Before Deploying
While AI-Powered Threat Detection is promising, implementation in reality requires more than a matter of plugging in a new gadget. It requires thoughtful planning, good governance, and proper infrastructure. The following are critical considerations in the path:
1.) Data Quality & Diversity
AI is only as good as the data it has learned from. Incomplete, outdated, or biased datasets can lead to false negatives – or worse, blind spots.
- Ensure access logs, behavior data, and contextual hints are clean, complete, and formatted consistently.
- Include both malicious and benign identity activity to prevent overfitting.
- Occasionally enrich data repositories—e.g., HR data, access policies, and device metadata—to enable richer context for analysis.
2.) Integration with Existing Ecosystems
The AI solution will need to integrate nicely with your identity and security stack to be of any use.
- Seek out native connectors or APIs to IAM, PAM, SIEM, EDR, and SOAR systems.
- Implement bi-directional data flow—so AI not only consumes intelligence but also responds by automating the responses.
- Ensure the solution has real-time event ingestion to make decisions in real-time.
3.) Explainability & Trust
Security teams need to know why the AI detected a session as suspicious.
- Select models with transparent decision trails, confidence scores, and contributing factors.
- Present AI output in a form that is easy for human analysts to review through visual dashboards or textual summaries.
- Establish trust in the system by cross-validation against known threats or past occurrences.
4.) Privacy, Ethics & Compliance
AI models tend to work with personal, behavioral, and contextual data—something that creates extremely serious questions regarding privacy and surveillance.
- Enforce compliance with laws such as GDPR, HIPAA, and local data residency laws.
- Establish explicit data governance rules that stipulate who gets to see what, when, and why.
- Investigate anonymization or tokenization of sensitive identity data that is used to train models.
5.) Human Readiness & Skills
AI is a force multiplier—not ever a replacement for security personnel.
- Upskill analysts to interact with AI tools, interpret output, and advise decision-making.
- Establish clear roles and responsibilities on when rely on automation and when to escalate to humans.
- Engage IAM, Security Operations, and Risk personnel early in the deployment process.
6.) Continuous Testing & Model Calibration
AI systems need to learn to deal with threats. That is:
- Continuous testing of performance metrics such as false positive rate, detection latency, and coverage.
- Model re-fitting or fine-tuning upon new behavior, applications, or users joining in.
- Simulated attacks (e.g., red teaming or breach and attack simulation) to optimize effectiveness.
Investing time to learn about these variables will not only make AI deployment more successful but drive ROI, resilience, and trust in the IAM strategy.
The Road Ahead: What’s Next for AI in IAM
As AI continues to evolve, its role in Identity and Access Management will shift from being an add-on to being an essential part. The following is a sneak peek into the future directions that will redefine how organizations leverage AI for identity protection:
🤝Federated Learning for Collective Intelligence
Instead of having every organization train their AI on their own, federated learning allows for shared training on shared platforms – without ever sharing raw data with each other. Decentralized, it enhances model accuracy without infringing on data privacy. Consider a threat seen on the network of one company making another company’s defense instantaneously stronger, all without violating confidentiality.
🔮Predictive Threat Modeling
At present AI detects anomalies. In future, AI will anticipate threats before they occur. By analyzing trends across millions of events over the years, AI will forecast probabilities of breaches, exposed identities, and vulnerable systems. This will allow IAM teams to shift from reactive mitigation to proactive fortification.
🤖Autonomous Response Systems
AI will shift from identifying threats to curing them automatically. These systems could quarantine a user’s account, revoke access permissions, reset passwords, or reverse malicious modifications—all without human intervention. Paired with human override, this will offer faster response times and less breach impact.
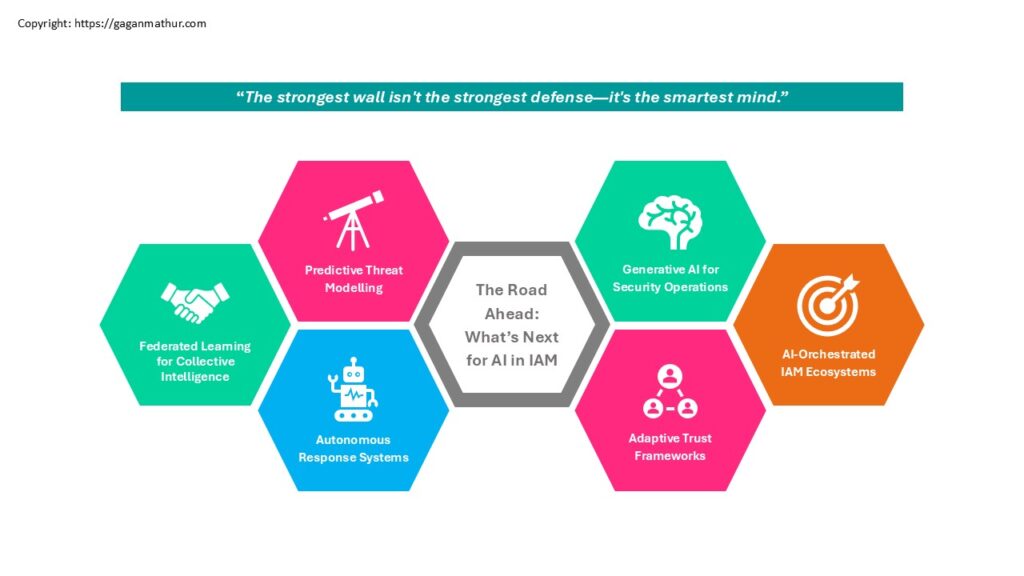
🧠Generative AI for Security Operations
Large Language Models (LLMs) and AI generative applications will assist SOC analysts more and more by threat summarization, incident reporting, and even crafting policy recommendations. This alleviates the workload from the analyst, so they can focus on high-impact decision-making.
🔁Adaptive Trust Frameworks
Future identity security will be Adaptive. Instead of static rules or periodic reviews, organizations will adopt adaptive models of trust where access decisions will evolve over time based on continuous risk assessments, intent recognition, and real-time behavioral signals.
🎯AI-Orchestrated IAM Ecosystems
AI will be the orchestrator – bringing IAM together with threat intelligence, endpoint information, user context, and access governance solutions. This meshed-together network will provide a genuinely unified and intelligent defense system, minimizing silos and response times.
Conclusion: From Reactive to Predictive
The path to intelligent, autonomous IAM is already in progress.
By adopting these AI innovations, organizations won’t only enhance security – they’ll future-proof their identity infrastructure for the next generation of innovation and threat evolution.
The threat environment of identity is changing at a faster pace than ever before – where yesterday’s playbooks simply don’t apply. Yesterday’s IAM platforms, though bedrock, are by nature reactive in nature – waiting to hear policy violation or user frustration before responding to it. AI-Driven Threat Detection is an existential change in thinking and possibility.
By infusing each access decision with intelligence, organizations can move from simple detection of breaches to anticipating and blocking them. From identifying suspicious login activity prior to a compromise being made to automatically responding to high-risk sessions in real-time, AI introduces speed, scale, and precision that manual methods simply can’t.
But this is not a technology-only ride – it’s one of trust, agility, and resilience. AI causes IAM systems to change and modify on a continuous basis, learn from every interaction, and evolve with evolving threats, user behavior, and regulations. Security is no longer a passive defensive bouncer but an engaged enabler of business innovation.
The future of IAM is one of thinking systems, learning systems, and acting systems. And AI is the intellect at the center of this revolution.
And so we end this episode, recalling: The strongest wall isn’t the strongest defense—it’s the smartest mind.
🔜 Stay tuned for Episode 4, where we dive into Post-Quantum Cryptography and explore how quantum advancements could redefine digital identity security.





