The fastest-growing population in the enterprise is not employees.
It is devices.
Sensors, cameras, industrial controllers, medical devices, vehicles, meters, robots, and software agents now connect to enterprise systems in numbers that far exceed human users. Many organisations manage millions of device identities, often without realising it.
From a CXO perspective, this changes the nature of security and governance entirely.
The question is no longer whether devices should be managed as identities.
The question is how leaders can govern them at scale, without slowing innovation or losing control.
Why Device Identity Has Become A Leadership Problem
Recent global incidents reveal a consistent pattern:
- Compromised devices using valid credentials
- Attacks moving laterally through trusted machine access
- Systems behaving “normally” until damage is done
- Investigations struggling to identify ownership or intent

In many cases, the breach did not exploit a software flaw.
It exploited unmanaged trust.
This is not a technical failure.
It is a governance failure.
What Real-World Incidents Are Telling Us
Across industries, the same lessons keep repeating:
- Manufacturing disruptions caused by compromised industrial controllers
- Healthcare incidents linked to unmanaged medical device access
- Smart city outages traced back to shared or static device credentials
Cloud breaches enabled by forgotten machine identities
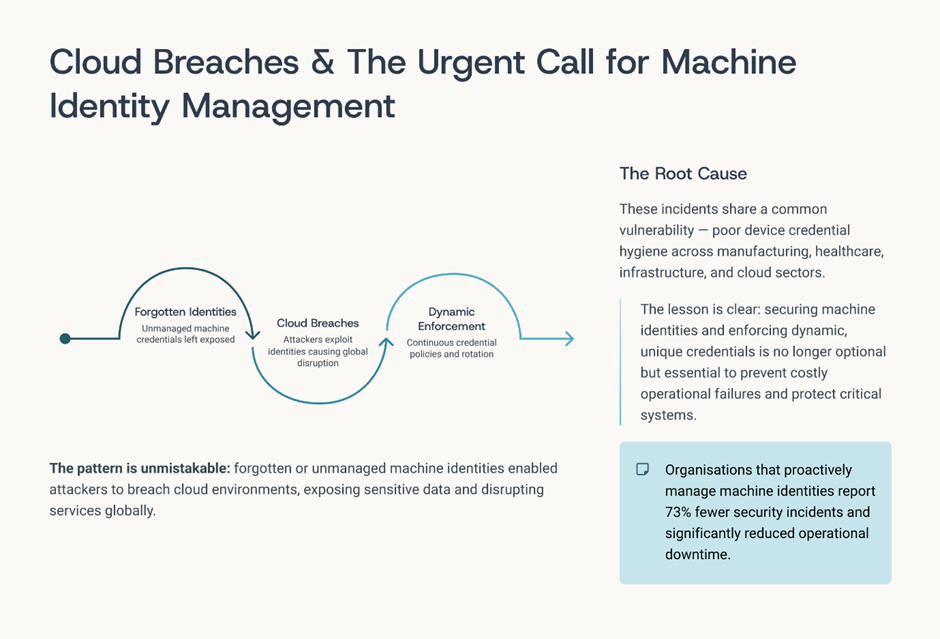
In almost every case:
- the device authenticated successfully
- Access was never revalidated
- trust never expired
The device did exactly what it was allowed to do.
Why Traditional IAM Models Break At Device Scale
Most IAM programs were designed for people.
They assume:
- onboarding events
- clear job roles
- manual approvals
- predictable behaviour
Devices don’t follow those rules.

They:
- connect continuously
- act autonomously
- change behaviour based on the environment
- outlive projects, vendors, and teams
Applying human IAM models to machines creates blind spots instead of control.
The Hidden Pain Leaders Are Already Feeling
CXOs rarely say this publicly, but it surfaces in private conversations:
- Device inventories are incomplete
- Ownership of device access is unclear
- Revocation happens late; or never
- Incident response lacks identity context
- Compliance reporting is fragmented
When something goes wrong, the first question is always the same:
“Who owns this device, and why was it still trusted?”
What Managing Millions Of Device Identities Really Requires
This is not about buying another tool.
It is about changing how identity is understood.
At scale, device identity management must focus on four leadership principles.

1. Treat every device as a first-class identity
Devices must be governed like users, not exceptions.
This means:
- Every device has a unique identity
- no shared credentials
- no anonymous access
- no “temporary” trust that becomes permanent
Why this matters:
- Ownership becomes clear
- Accountability becomes possible
- Incidents can be traced quickly
At scale, uniqueness is not overhead.
It is control.
2. Design identity for the full device lifecycle
Most device risk exists after deployment.
Leaders must ensure identity governance spans:
- provisioning
- activation
- updates
- role changes
- decommissioning
Common failures include:
- devices surviving project completion
- vendor access persists indefinitely
- retired devices retaining credentials
Lifecycle governance reduces:
- attack surface
- cloud resource waste
- audit exposure
An identity that doesn’t expire becomes a liability.
3. Shift from static trust to continuous validation
Static credentials are the weakest link in device security.
Modern device IAM must:
- validate behaviour continuously
- reassess trust as conditions change
- restrict access automatically when risk rises
This does not require human intervention at every step.
It requires policy-driven, real-time decisioning.
The goal is simple:
Trust devices when they behave as expected.
Challenge them when they don’t.
4. Govern device access by impact, not volume
Not all devices matter equally.
Leadership teams must prioritise:
- devices controlling critical infrastructure
- systems with safety implications
- identities with broad system access
- machines that can cause cascading failure
Managing millions of devices does not mean treating them all the same.
It means focusing governance where consequence is highest.
Why Machine Identity Governance is a CXO Responsibility
Device identities intersect with:
- operational continuity
- public safety
- regulatory compliance
- brand reputation
- national infrastructure

Delegating this purely to engineering teams creates gaps.
When leadership owns the identity model:
- priorities align
- accountability sharpens
- response accelerates
- trust becomes defensible
This is governance, not configuration.
What Forward-Looking Organisations Are Doing Differently
Organisations managing device identities well share common traits:
- unified visibility of human and machine identities
- clear ownership of device access decisions
- automated revocation tied to lifecycle events
- fewer static credentials
- faster containment when anomalies occur
They are not perfect.
They are intentional.
Why AI And Automation Matter, But Are Not The Solution Alone
AI and automation are becoming essential as identity environments scale beyond what humans can reasonably manage. When organisations are dealing with millions of users, devices, and access decisions, manual processes simply cannot keep up. AI helps detect patterns, spot anomalies, and respond faster than any security team could on its own. Automation reduces dependency on repetitive human actions and enables systems to operate continuously, even as environments grow more complex.
However, treating AI and automation as a complete solution is where many organisations go wrong. These technologies amplify whatever design they are built upon. If identity ownership is unclear, access rules are poorly defined, or governance is fragmented, AI will not fix those problems; it will accelerate them. Faster decisions are only valuable when they are the right decisions.
From a leadership perspective, AI and automation should be seen as force multipliers, not replacements for accountability and intent.
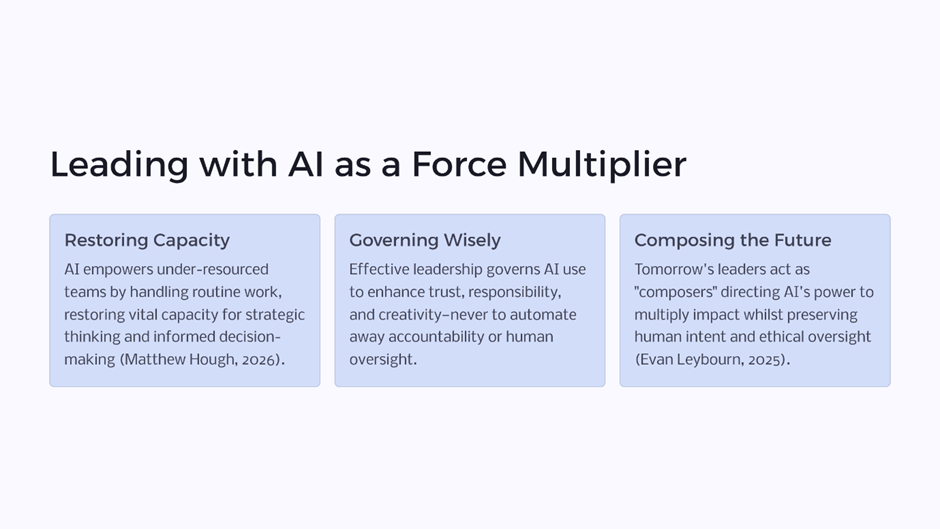
They add value when:
- Identity foundations are clean, with clear ownership of users, devices, and access privileges.
- Policies are well-defined, so automated decisions reflect business risk, not just technical signals.
- Lifecycle governance is in place, ensuring identities and access expire naturally when no longer needed.
- Exceptions are intentional, not the result of unmanaged complexity.
They fall short when:
- Automation is layered on top of broken or outdated processes.
- AI is expected to compensate for missing governance.
- Decisions are delegated entirely to systems without human oversight.
- Speed is prioritised over correctness and accountability.
The most successful organisations use AI to enhance judgment, not replace it. Automation handles scale and consistency, while leaders define boundaries, ownership, and acceptable risk. In this model, AI becomes a trusted assistant, surfacing insight, accelerating response, and reducing noise, while humans remain responsible for intent and direction.
Ultimately, sustainable security is not achieved by choosing between people and machines. It is achieved by designing systems where technology executes efficiently, and leadership governs wisely.
The Future: From Device Control To Trust Control
The future enterprise will not ask:
“Is this device allowed?”
It will ask:
- Should this device be trusted right now?
- Does its behaviour still match its purpose?
- Has its risk profile changed?
This shift, from access control to trust control, is what allows identity governance to scale into the millions.

An Optimistic Way Forward
Managing millions of device identities is not an impossible task.
It becomes manageable when leaders:
- accept that devices are identities
- design for lifecycle, not onboarding
- replace permanent trust with contextual trust
- align governance with real-world impact
Small design changes, applied consistently, deliver:
- reduced breach risk
- faster response
- clearer accountability
- safer innovation
Final Words
Devices will continue to multiply across every industry, quietly embedding themselves into daily operations, infrastructure, and decision-making systems. They already act faster than humans, make autonomous choices, and interact with critical environments without waiting for approval or oversight. As this machine-driven layer grows, it will increasingly shape outcomes that matter deeply: operational continuity, public safety, customer trust, and even regulatory standing. In this reality, success will not belong to organisations that simply deploy the highest number of connected devices or adopt the latest technology first. It will belong to those who understand something more fundamental: that every device represents a decision to trust. Without clear identity governance, that trust becomes blind, persistent, and dangerously difficult to revoke.
Managing millions of device identities, therefore, is not merely an exercise in scale or automation. It is about making deliberate choices around who or what is allowed to act, under which conditions, and for how long. It requires designing systems where trust is earned, continuously evaluated, and withdrawn when context changes. This level of intentional trust cannot be delegated entirely to tools or buried inside technical teams. It demands leadership clarity; clear ownership, clear accountability, and a willingness to treat identity as a strategic control rather than a background function. Ultimately, how an organisation governs device identities reflects how seriously it takes responsibility in a machine-driven world. And that, unmistakably, is a leadership decision.






