For a long time, organisations believed that if they invested enough in security tools, threats would eventually be contained. Firewalls were strengthened. Detection engines became faster. Dashboards multiplied.
Yet incidents continued.
What changed was not the intent of attackers, but where they chose to strike.
Today, most serious cyber incidents no longer begin with broken systems. They begin with trusted identities behaving in unexpected ways. That shift has quietly pushed identity to the centre of modern security, and exposed a gap many leaders are still struggling to close.
This is where AI is starting to matter, not as another layer of technology, but as a way to unify threat and identity defence into a single, coherent system.
1. The Reality Leaders Are Facing Today
Across industries, security leaders are dealing with the same uncomfortable pattern:
- Alerts are increasing, but clarity is not
- Identity incidents are detected late, not early
- Valid credentials are misused without triggering alarms
- Access remains active long after risk has changed
- Teams respond fast, but only after damage has begun
The frustration is not a lack of effort.
It is a lack of context.
Security teams see activity.
Identity teams see access.
But the two rarely converge at the moment decisions matter most.
2. Why Identity Has Become the Primary Attack Path

Recent incident analyses across enterprises reveal a consistent trend:
- Stolen or misused credentials are the starting point
- Privileges are exploited, not escalated forcefully
- Behaviour blends into “normal” patterns
- Detection happens only after lateral movement
This is why identity-based attacks are so effective. They do not look like attacks. They look like business as usual, until they aren’t.
Traditional security tools were not designed for this. They were built to spot malicious actions, not misplaced trust.
3. The surprising pain point nobody likes to admit
Here is the reality many CXOs quietly acknowledge but rarely say aloud:
"Most security failures today are not technical failures.
They are decision failures."
Decisions such as:
- keeping access active “just in case”
- approving privileges without understanding the impact
- trusting identities indefinitely
- reacting to alerts without knowing intent
The systems did exactly what they were designed to do.
They just weren’t designed to think together.
4. Why AI Changes the Equation: If Used Correctly

AI is often discussed as a tool for speed or automation. That framing is incomplete.
The real value of AI in unified threat and identity defence lies in its ability to connect signals that humans and siloed systems cannot process together promptly.
AI does not replace security teams or identity and access management (IAM) teams.
It augments judgment where scale and complexity overwhelm human response.
5. What Unified Threat and Identity Défense Actually Means
Unified defence is not about merging teams or buying a single platform.
It is about ensuring that:
- identity signals inform threat detection
- threat signals influence access decisions
- trust is continuously reassessed
- response happens before escalation
AI becomes the connective tissue that makes this possible.
6. How AI Strengthens Identity as a Security Control
AI improves identity defence in ways traditional rules cannot:
i. Continuous Trust Assessment
Instead of trusting an identity because it was verified once, AI evaluates:
- behaviour consistency
- access patterns
- context changes
- risk signals over time

Trust becomes dynamic, not permanent.
ii. Early Detection of Identity Drift
AI detects subtle deviations such as:
- unusual access timing
- unexpected system usage
- abnormal privilege use
These signals often appear before an incident is visible to traditional tools.
iii. Risk-Based Access Adjustment
Rather than blocking everything or allowing everything, AI enables:
- step-up verification when risk rises
- privilege reduction when behaviour changes
- friction only when necessary
This protects security without exhausting users.
7. How AI Helps Security Teams Act with Precision
For most security teams today, the problem is not a lack of alerts; it is an excess of them. Dashboards are full. Notifications are constant. Yet clarity is rare. When everything looks urgent, nothing truly is.

AI changes this dynamic by shifting security operations from volume-driven reaction to precision-driven decision-making.
Instead of forcing teams to chase every signal, AI helps them focus on what actually matters.
AI Reduces Noise Without Losing Visibility
Traditional security tools surface activity based on rules and thresholds. AI adds context.
It filters signals by understanding:
- historical identity behaviour
- access patterns over time
- normal versus abnormal usage
- correlation across identity and system events
This allows security teams to see fewer alerts, but better ones.
✓ AI Identifies Which Identities Matter Most
Not all identities carry the same risk.
AI helps security teams prioritise:
- privileged accounts
- high-impact business roles
- identities with broad system reach
- users whose access spans multiple environments
Instead of treating all users equally, security teams can focus on identity impact, not just activity volume.
✓ AI Distinguishes Risky Behaviour from Normal Work
One of the hardest challenges in modern security is separating malicious behaviour from legitimate work.
AI evaluates:
- unusual login timing
- unexpected access sequences
- abnormal system combinations
- deviation from personal behavioural baselines
This reduces false positives and prevents security teams from escalating routine activity unnecessarily.
✓ AI Flags Access That Requires Immediate Challenge
Rather than waiting for an incident, AI can signal when:
- Access should be revalidated
- Privileges should be reduced temporarily
- Step-up authentication is needed
- Sessions should be monitored more closely
These actions happen before damage escalates, not after.
✓ AI Improves Speed Without Sacrificing Judgment
Speed alone is not enough. Fast mistakes are still mistakes.
AI supports decision-making by:
- presenting risk context alongside alerts
- explaining why a signal matters
- ranking actions by potential impact
This helps analysts respond confidently instead of hesitating or overreacting.
8. The Result: From Firefighting to Focused Intervention
When AI is applied correctly:
- security teams spend less time triaging noise
- investigations become shorter and clearer
- response actions are more targeted
- burnout decreases
- confidence increases
Security shifts from being loud and reactive to quiet, deliberate, and effective.
From a leadership perspective, this is the real value of AI. Not automation for its own sake, but clarity at scale. When security teams know where to look, when to act, and why it matters, prevention becomes possible. And prevention, not response, is where modern security must ultimately operate.
9. Real-World Pattern: What Changes When Identity and Threat Data Converge
Organisations that align identity and threat signals consistently see:
- Faster containment of incidents
- Reduced blast radius from compromised accounts
- Fewer false positives
- Clearer accountability for access decisions
- Improved audit and compliance outcomes
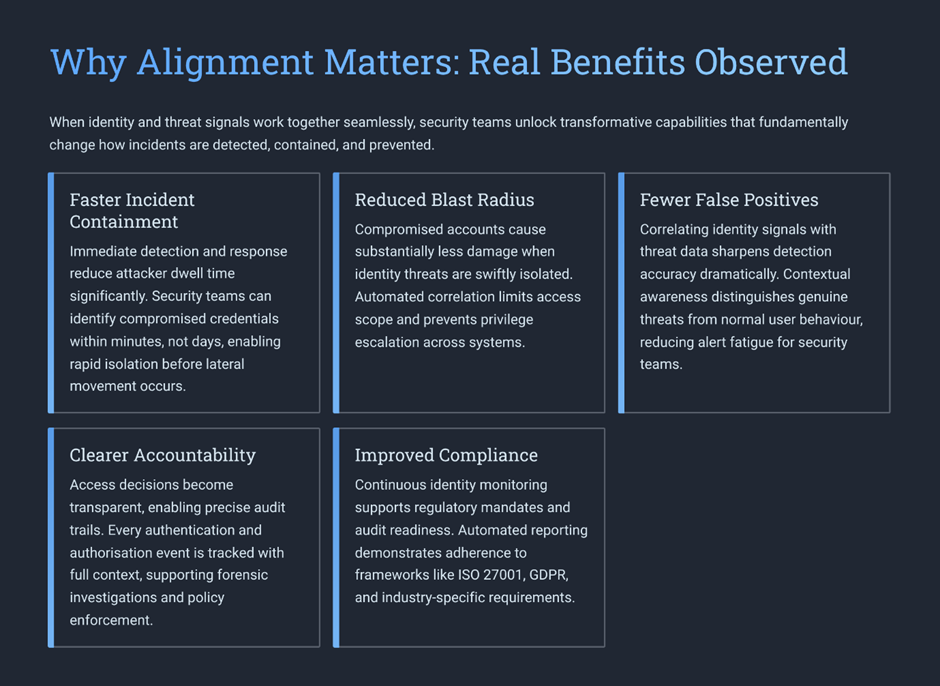
Not because threats disappeared, but because trust was challenged earlier.
10. Where Many Organisations Go Wrong with AI
The most common mistakes are not technical. They are strategic:
- Treating AI as a bolt-on instead of a redesign
- Automating poor processes faster
- Ignoring human experience
- Expecting AI to “fix” fragmented ownership

AI amplifies design.
If design is fragmented, AI scales the problem.
11. The Leadership Shift Required
Unified threat and identity defence does not begin with tools, platforms, or AI models. It begins with leadership alignment and ownership of trust. Without that, even the most advanced technology only automates fragmentation.
For too long, identity has been treated as an operational concern and security as a technical safeguard. That separation has created a dangerous blind spot at the leadership level. When no one owns trust holistically, it is managed in pieces, and attackers thrive in the gaps.
Leaders must move beyond surface-level questions about coverage and start asking more fundamental ones:
- How confident are we in the identities we trust today, not just at onboarding, but right now?
- How quickly does trust adjust when behaviour, context, or risk changes?
- Do our security decisions reflect real-time identity context, or are they reacting after the fact?
These questions are not technical diagnostics. They are governance questions. When they are asked and answered at the executive level, priorities change. Teams collaborate differently. Identity data flows where it needs to. Security decisions become proactive rather than reactive.
In that environment, AI stops being a patch for complexity and becomes what it was always meant to be: an enabler of better, faster decisions. Not a crutch to compensate for unclear ownership, but a force multiplier for leadership intent.
That shift, more than any tool, defines whether unified defence succeeds or quietly fails.
12. The Human Factor Still Matters
One concern leaders often raise is friction.

The truth is counterintuitive:
AI reduces friction when identity and threat data are unified.
Because:
- low-risk users are left alone
- high-risk behaviour is challenged early
- blanket controls are replaced with precision
Security becomes quieter and more effective.
The Path Forward: From Fragmented Defence to Unified Confidence
The future of cybersecurity is not about more alerts or tighter controls.
It is about:
- understanding identity continuously
- challenging trust intelligently
- acting early instead of loudly
- designing security that adapts as fast as the business does
AI makes this possible, not by thinking for leaders, but by giving them better insight at the moment it matters.
Way Ahead
Despite the challenges, this is a promising moment.
For the first time, organisations have the capability to:
- see identity and threat as one system
- prevent incidents instead of explaining them
- protect trust without sacrificing speed
- align security with business reality
Unified threat and identity defence is not a distant vision.
It is already taking shape where leadership intent meets intelligent design. AI simply helps us make them sooner.






